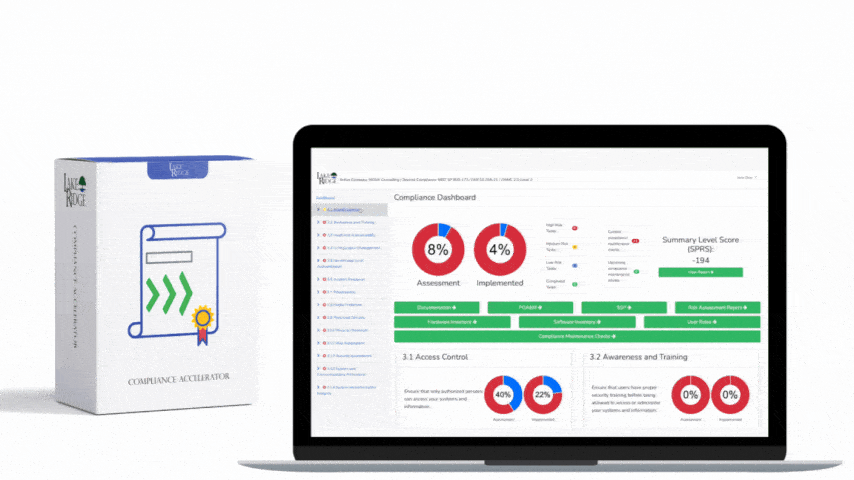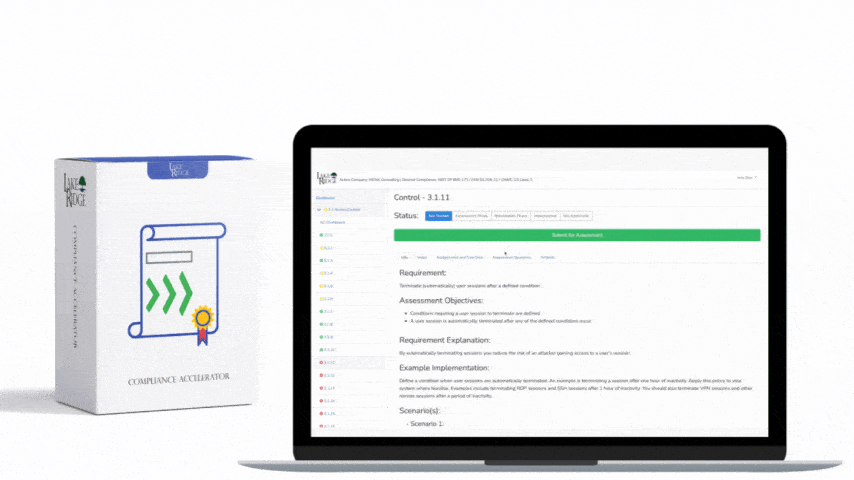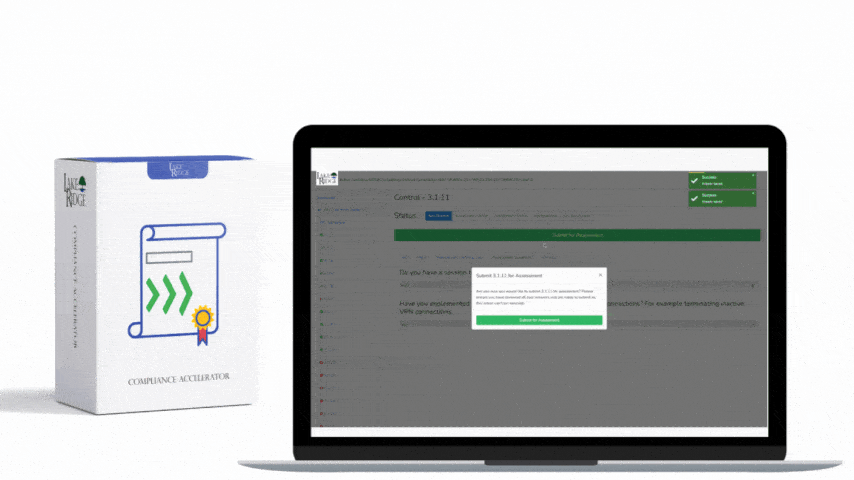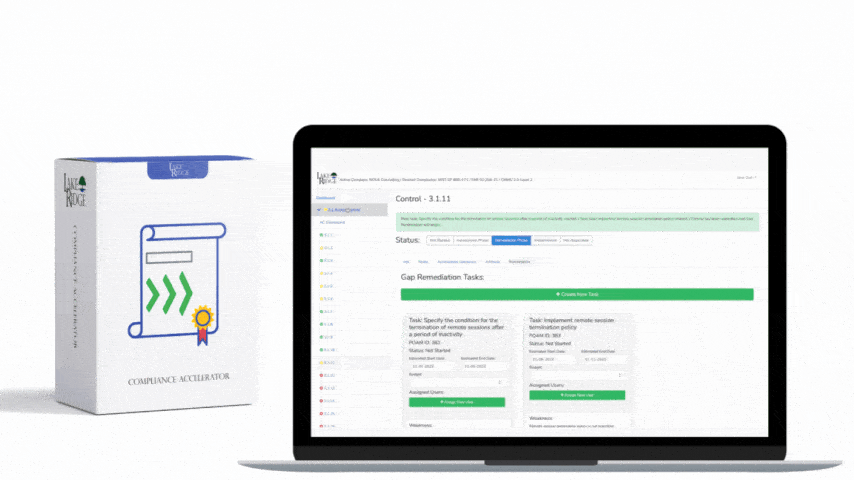
CMMC 1.0 Practice AC.2.009 Requirement:
Limit unsuccessful logon attempts.
CMMC 1.0 AC.2.009 Requirement Explanation:
By locking an account after several consecutive failed logon attempts you prevent brute-force attacks. An account lockout can be triggered by a legitimate user incorrectly entering their password. To give them another chance to try logging in again you can configure your accounts to automatically unlock after a set period of time (e.g., 5 minutes). By allowing accounts to automatically unlock after several minutes you can reduce IT ticket loads, otherwise IT staff may be kept busy unlocking user accounts.
Example CMMC 1.0 AC.2.009 Implementation:
Configure your user accounts to lock after consecutive failed logon attempts. Locking an account after three failed attempts is a common setting. Set your accounts to unlock after several minutes or require your admins to manually unlock accounts.
CMMC 1.0 AC.2.009 Scenario(s):
- Scenario 1:
John, an employee at your company incorrectly entered his password three times in a row, resulting in his account being locked. John submits a help desk ticket requesting an account unlock. Your IT staff asks him to wait 5 minutes for the account to unlock. 5 minutes later John has remembered his password and is able to log in.
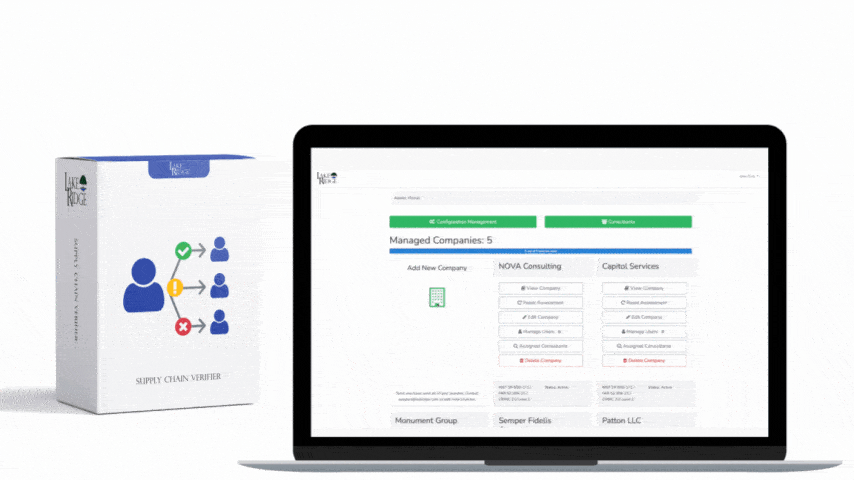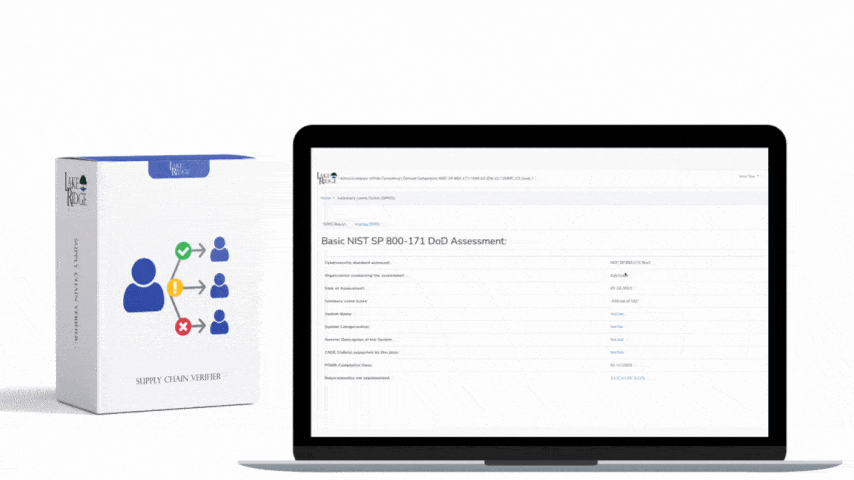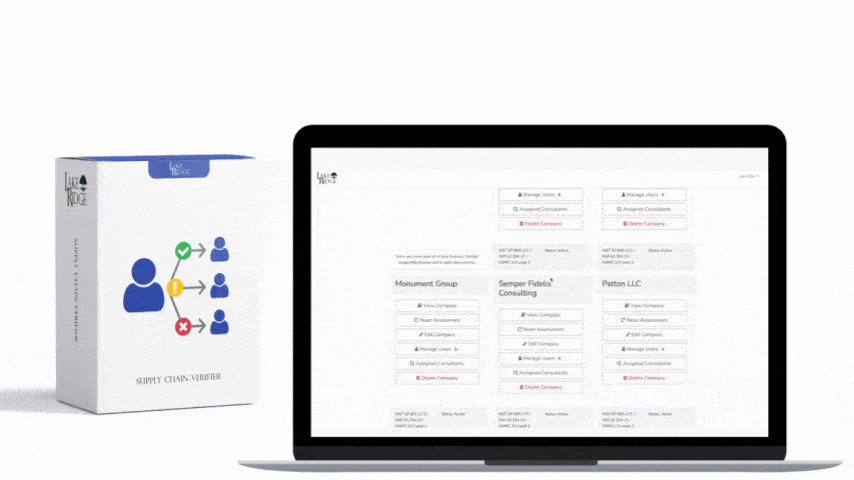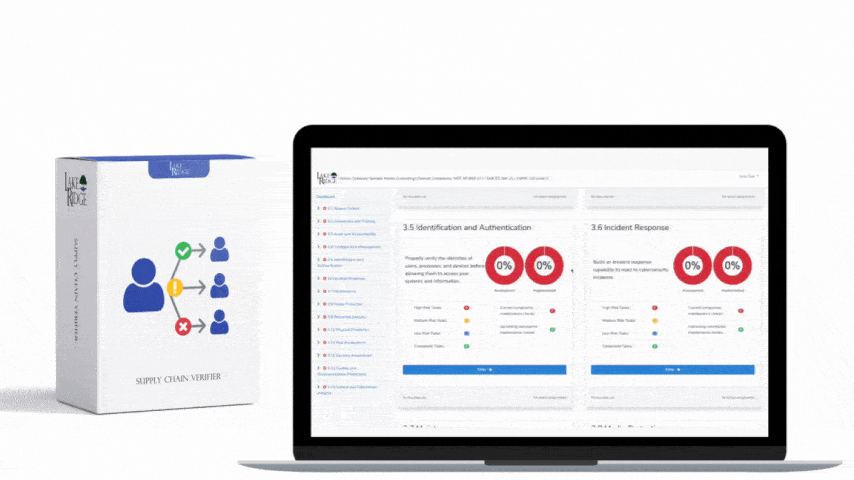
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you