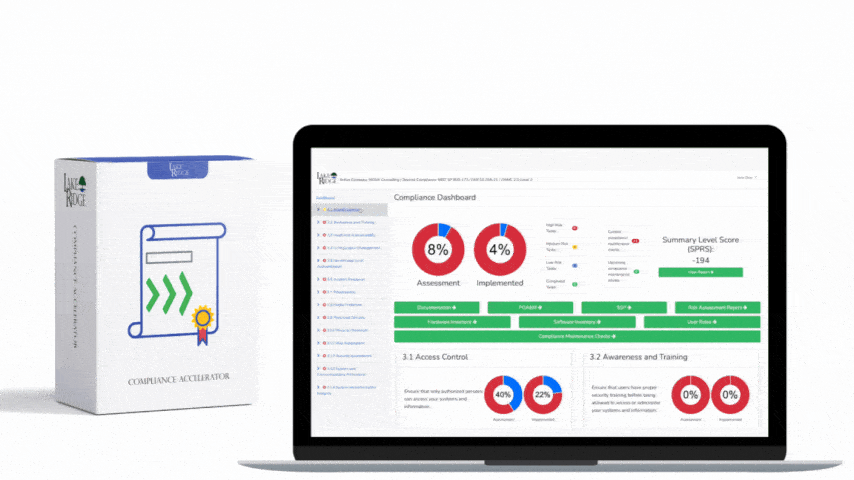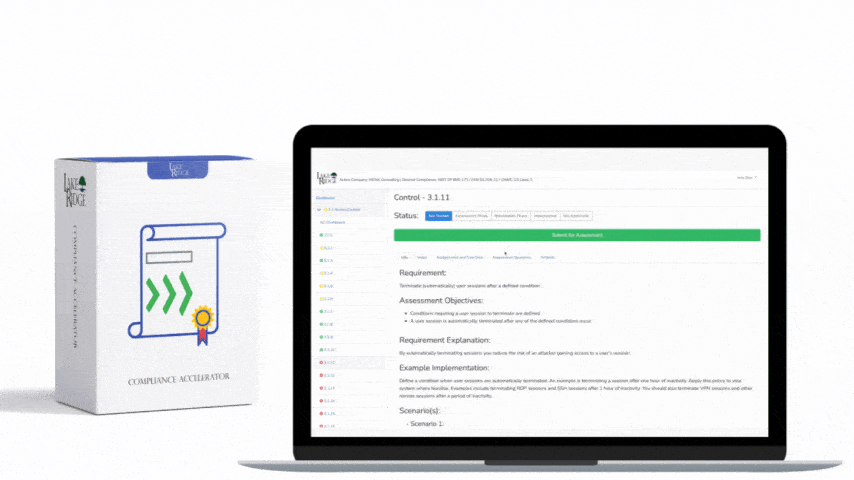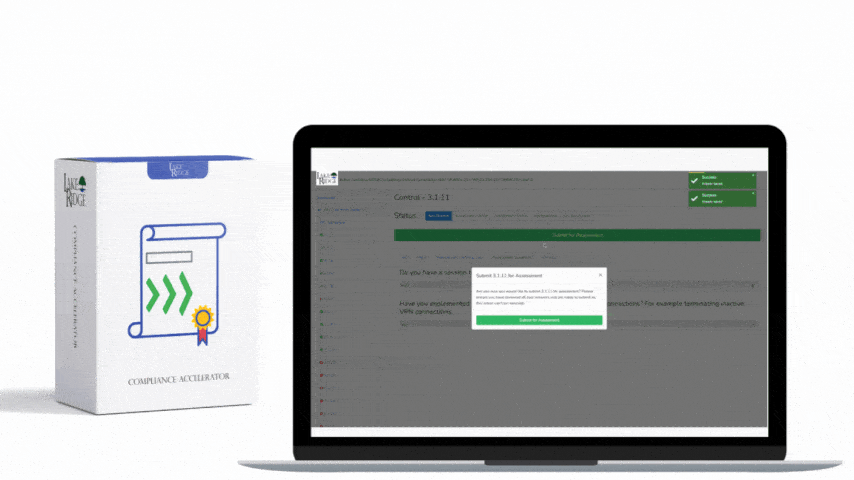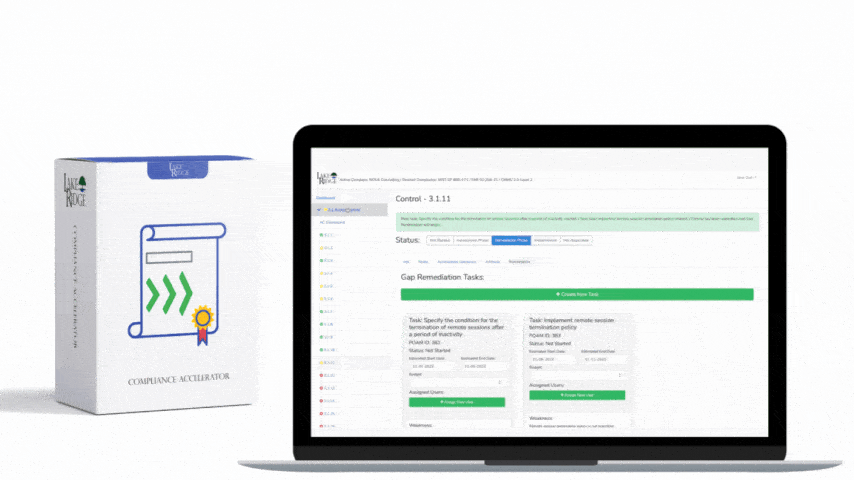
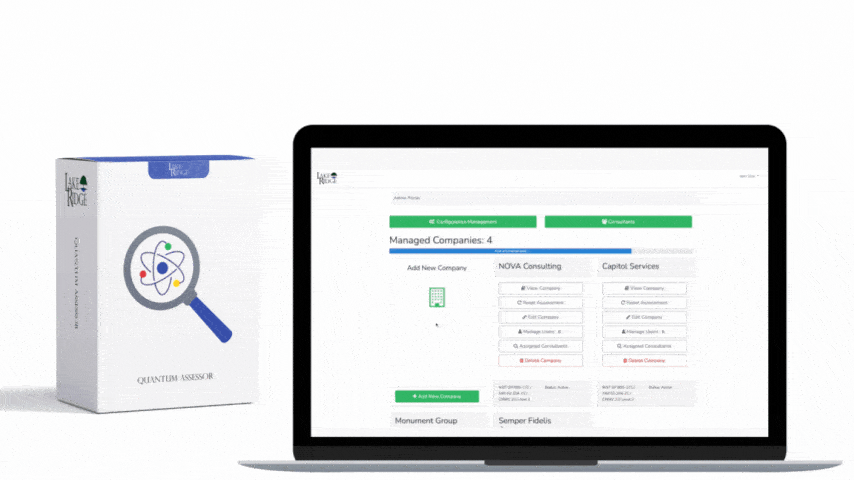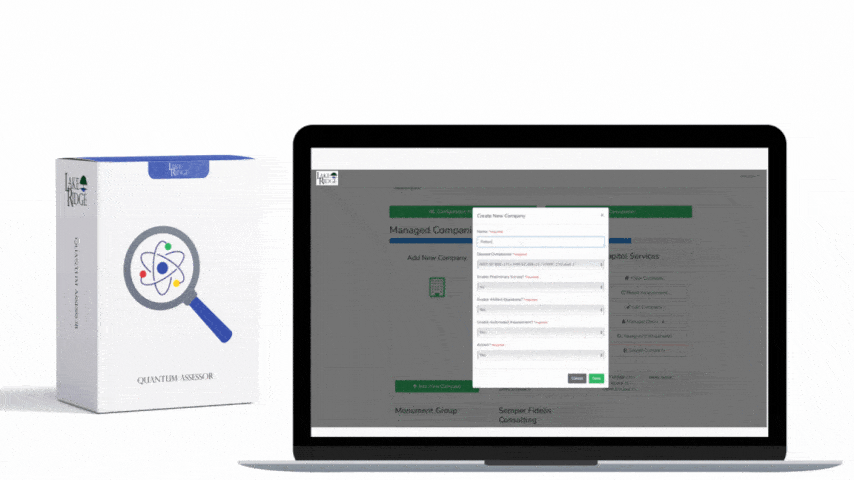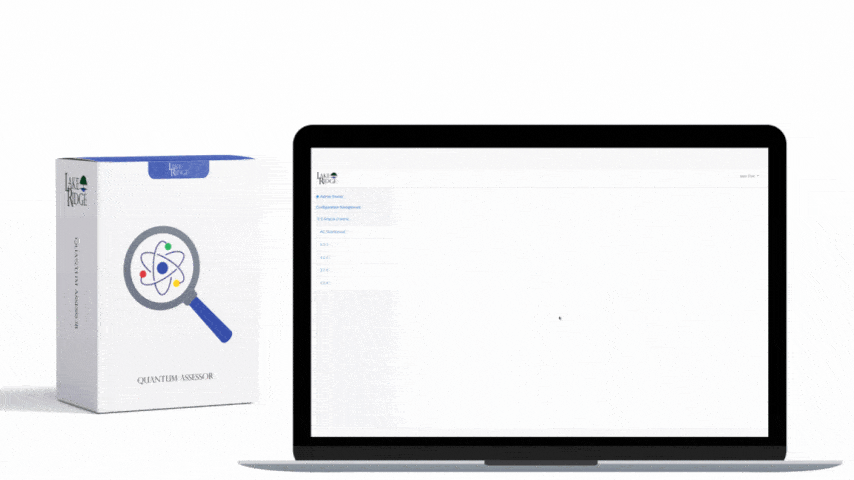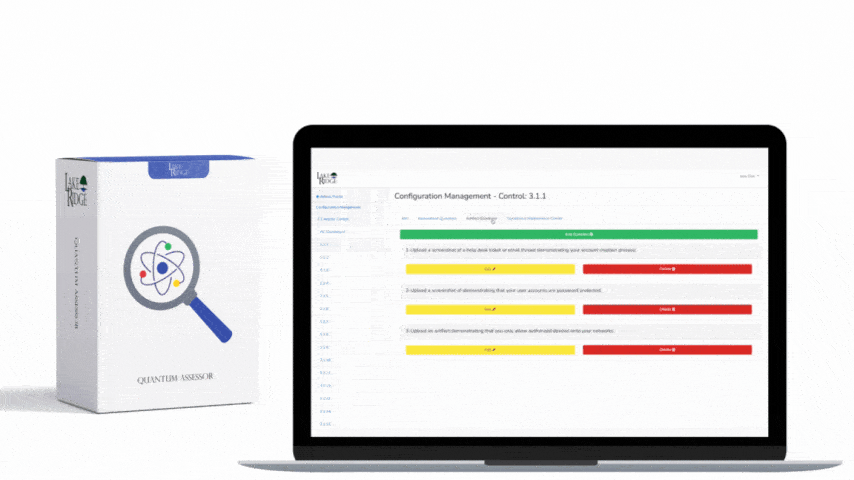
CMMC 1.0 Practice AU.2.041 Requirement:
Ensure that the actions of individual system users can be uniquely traced to those users so they can be held accountable for their actions.
CMMC 1.0 AU.2.041 Requirement Explanation:
In the event of a security incident you will need to review system logs to trace events back to a user. If your systems are not configured to capture the appropriate logs you will not be able to identify which account committed the security incident.
Example CMMC 1.0 AU.2.041 Implementation:
Your systems need to capture logs that can aid in tracing actions back to a user. Your logs should capture user IDs, source and destination IP addresses, and time stamps.
CMMC 1.0 AU.2.041 Scenario(s):
- Scenario 1:
Alice, a system administrator wants to determine which users are connecting to her network via the VPN. To accomplish this she configures her VPN to capture the following information: Username, computer/machine name, time stamp, source and destination IP address. Using the above logs she can trace VPN connections back to a specific individual.
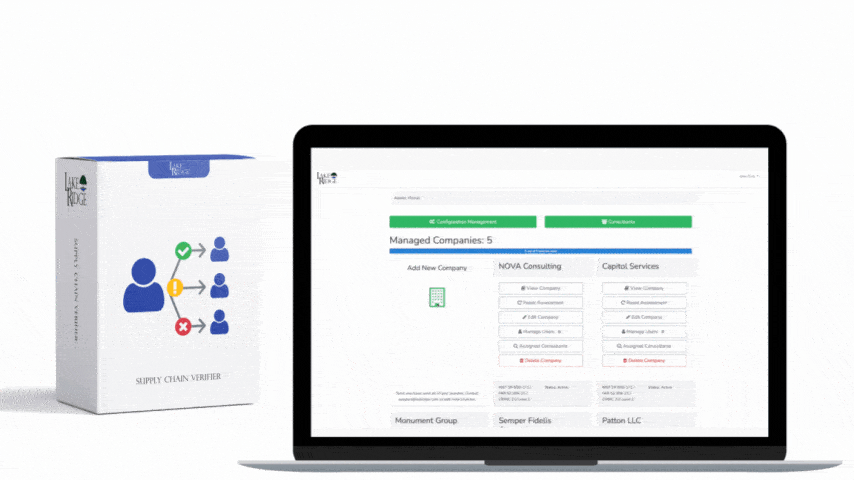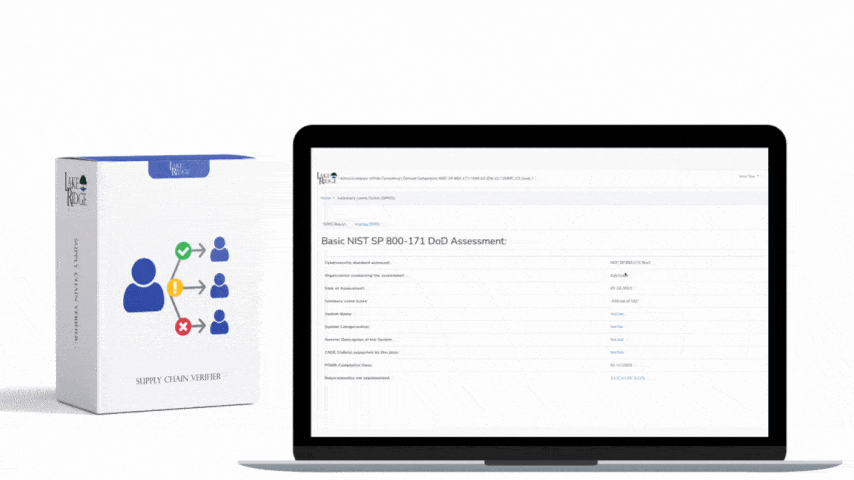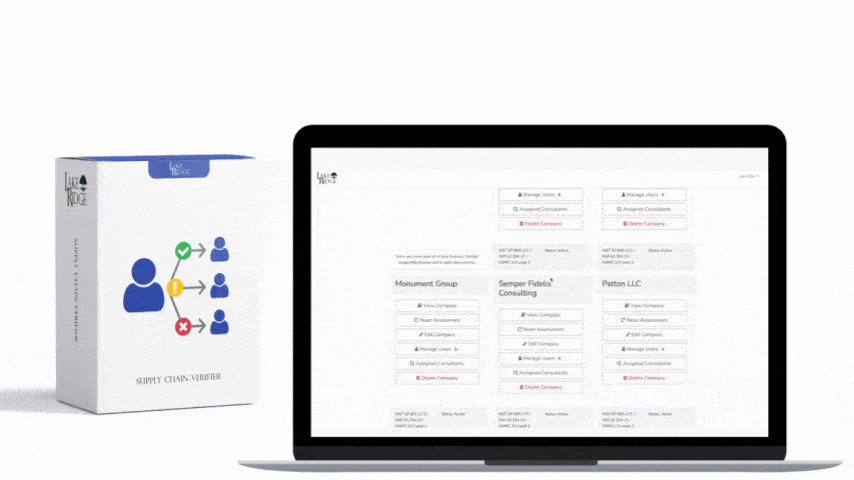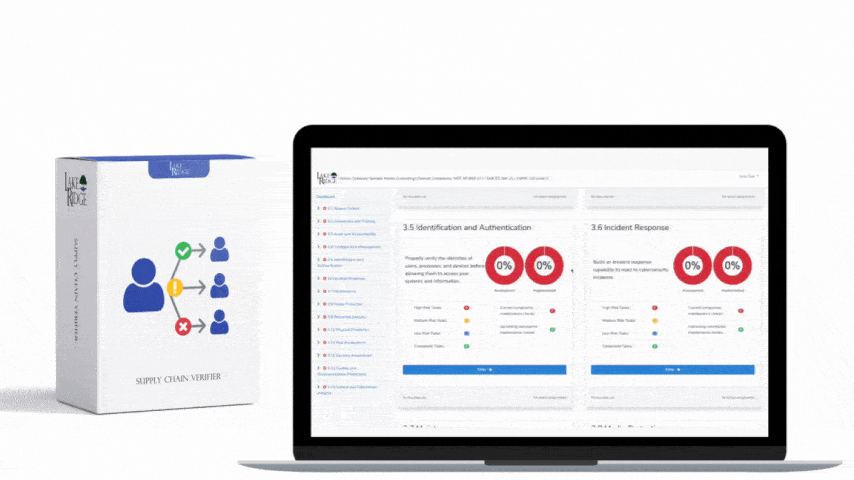
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you