CMMC 1.0 Practice CA.2.158 Requirement:
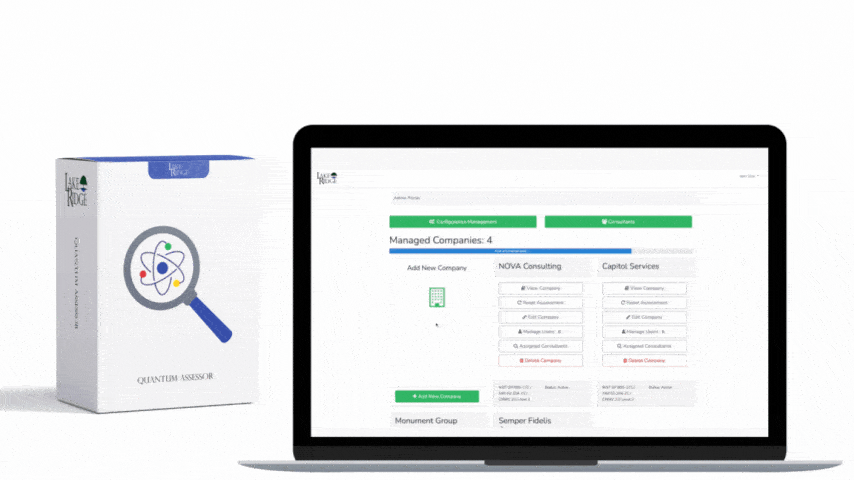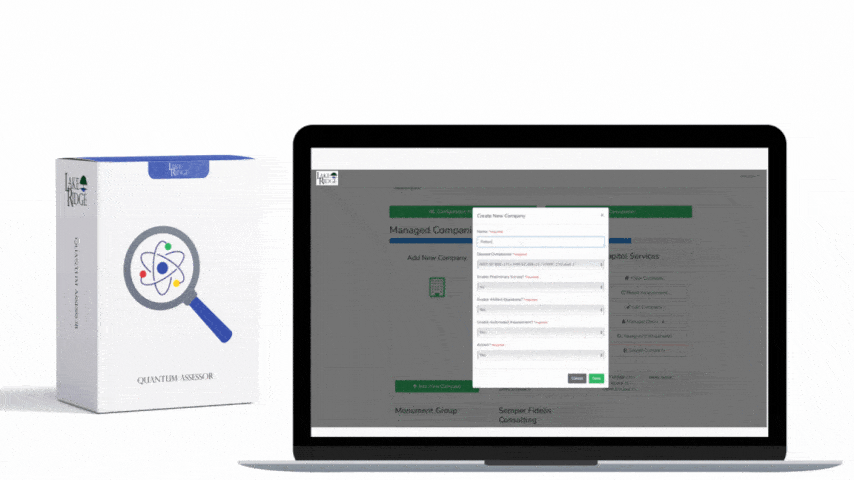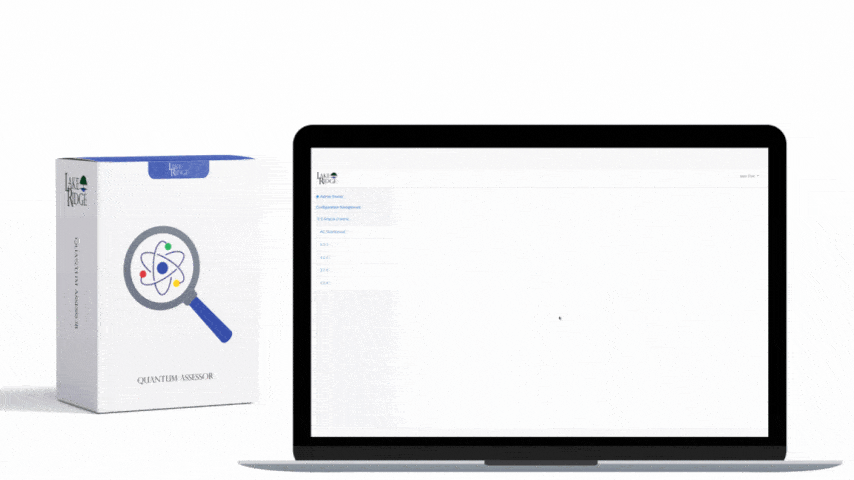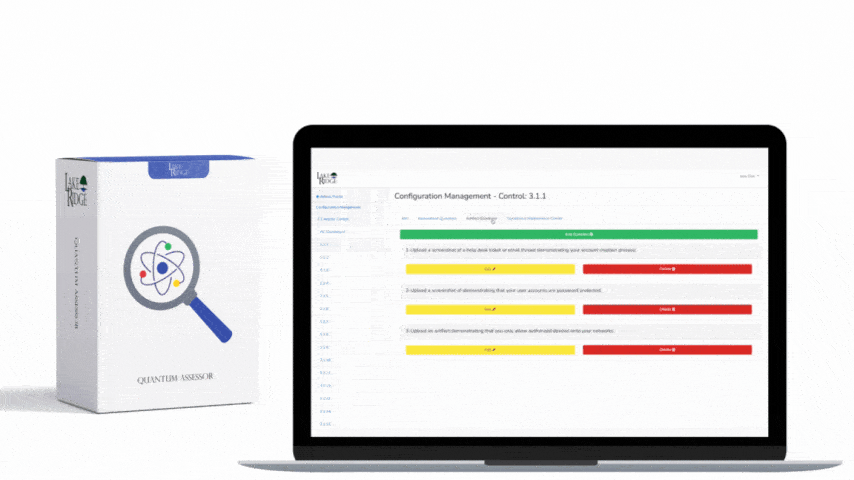
Periodically assess the security controls in organizational systems to determine if the controls are effective in their application.
CMMC 1.0 CA.2.158 Requirement Explanation:
By assessing your security controls you can identify issues before an attacker can exploit them. You will also be prepared to meet DoD compliance requirements.
Example CMMC 1.0 CA.2.158 Implementation:
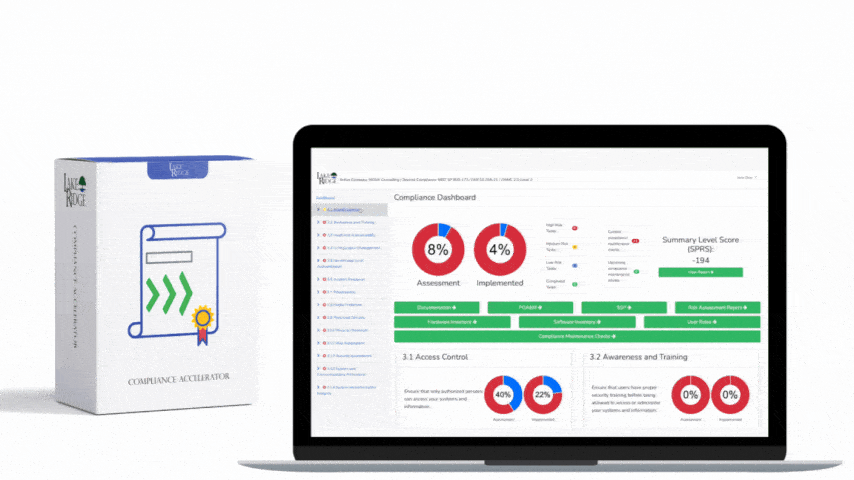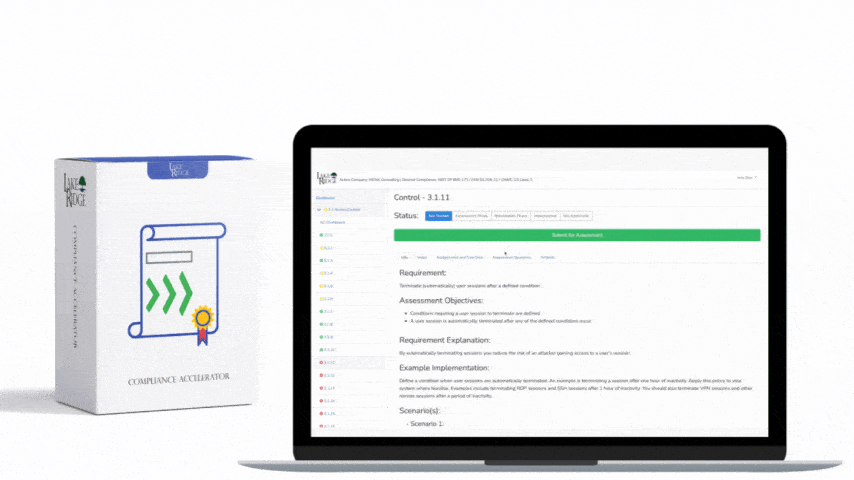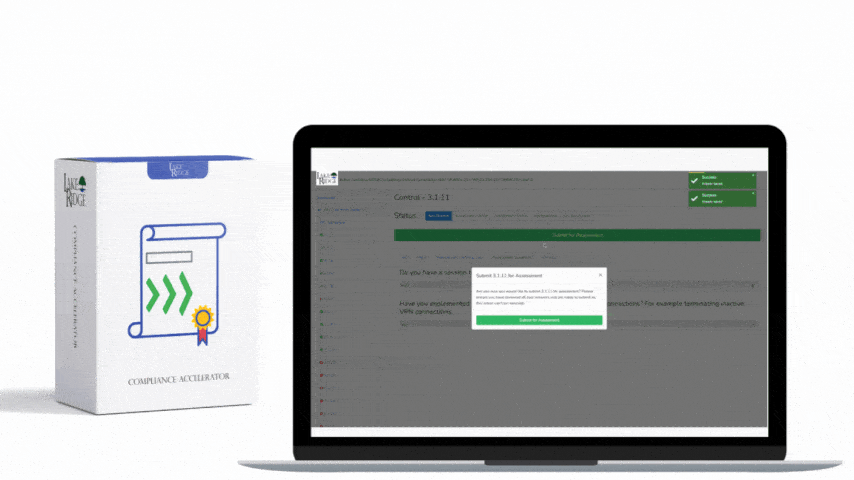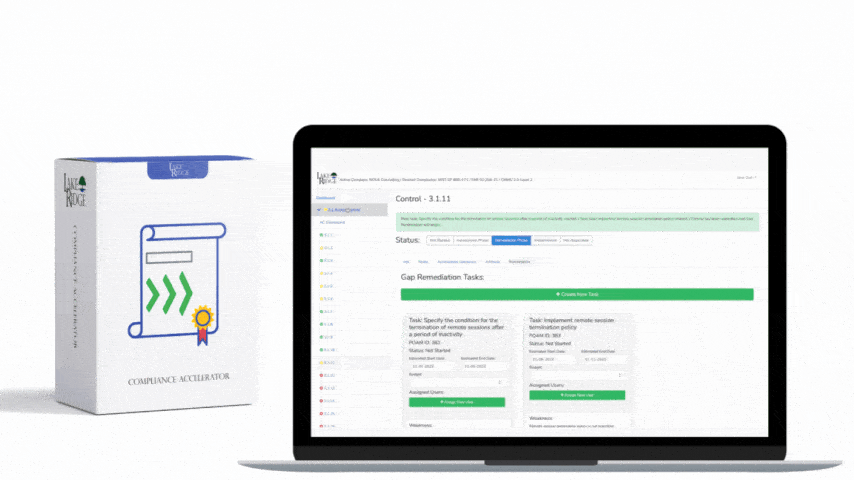
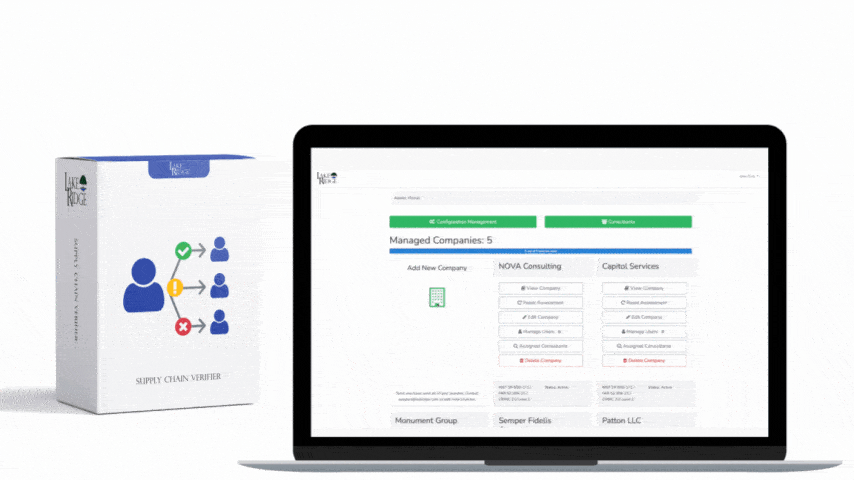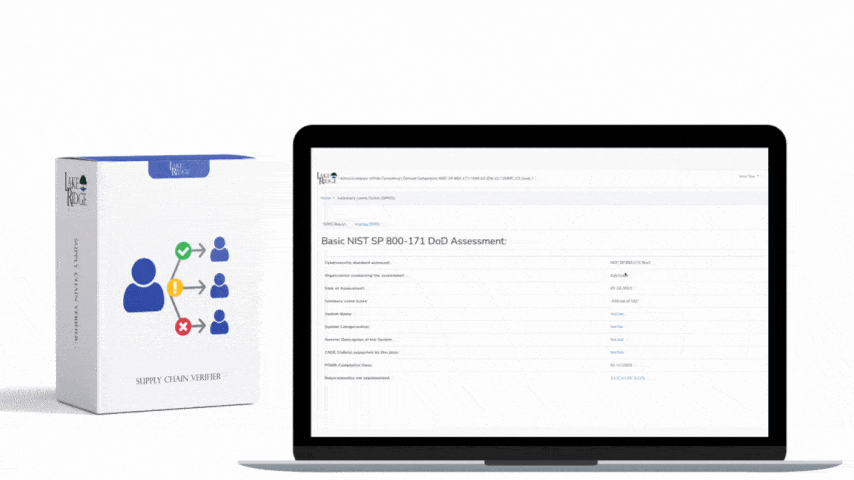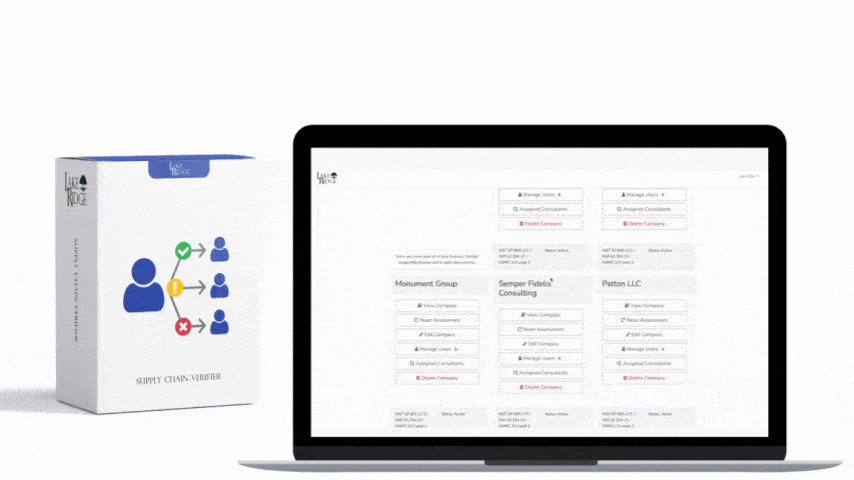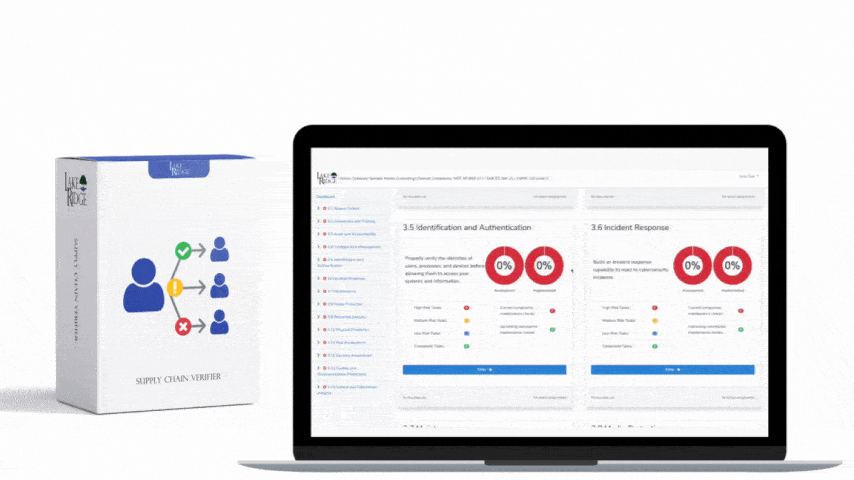
By undergoing this gap analysis your are meeting this control. Your security controls are being assessed for their effectiveness and gaps are identified. You should periodically (e.g. annually) assess your security controls and make improvements as needed. The assessments can be conducted internally, you are not required to hire a third party.
CMMC 1.0 CA.2.158 Scenario(s):
- Scenario 1:
Your company wants to determine the effectiveness of its cybersecurity program which is built to meet CMMC requirements. You hire a third party to conduct an assessment to determine if you are meeting requirements and if your controls are effective. The third party provides you with a report with recommendations on improving your security program.
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you