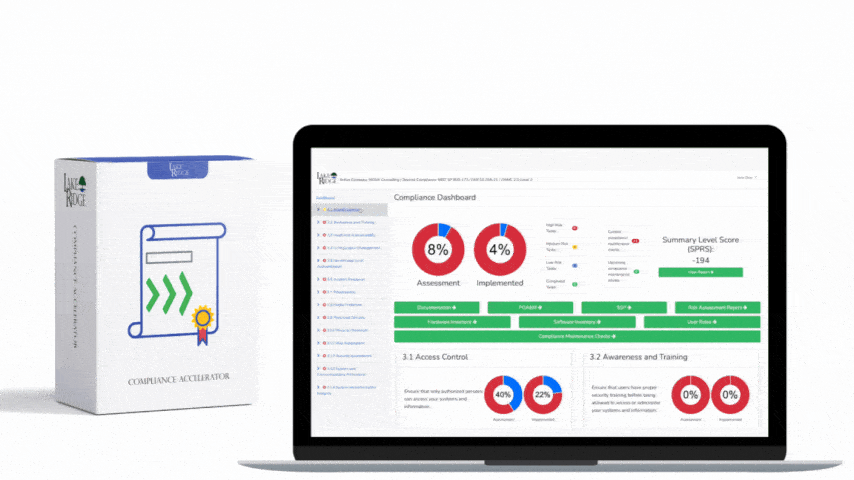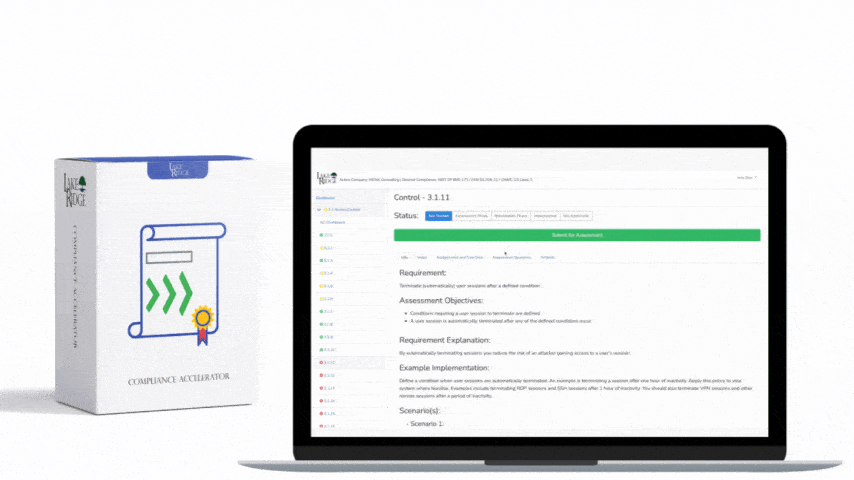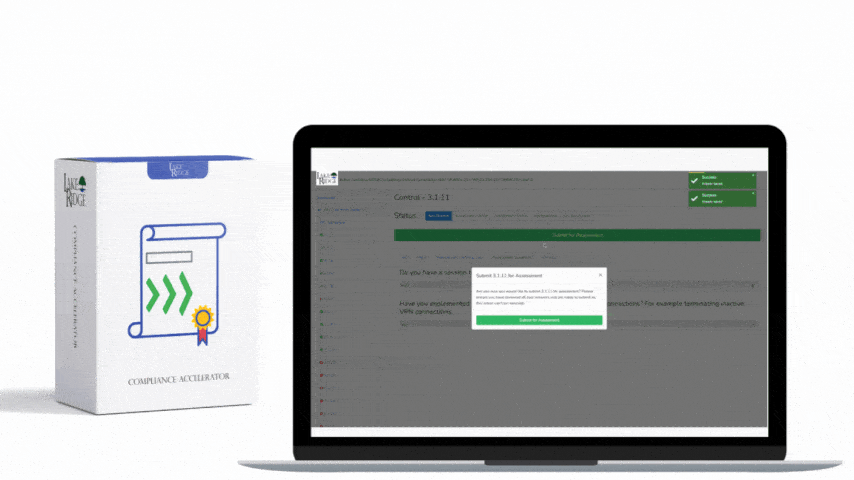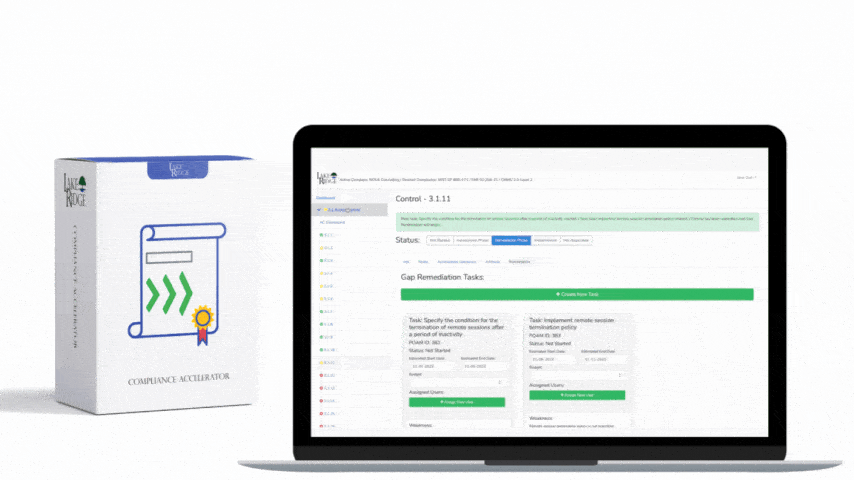
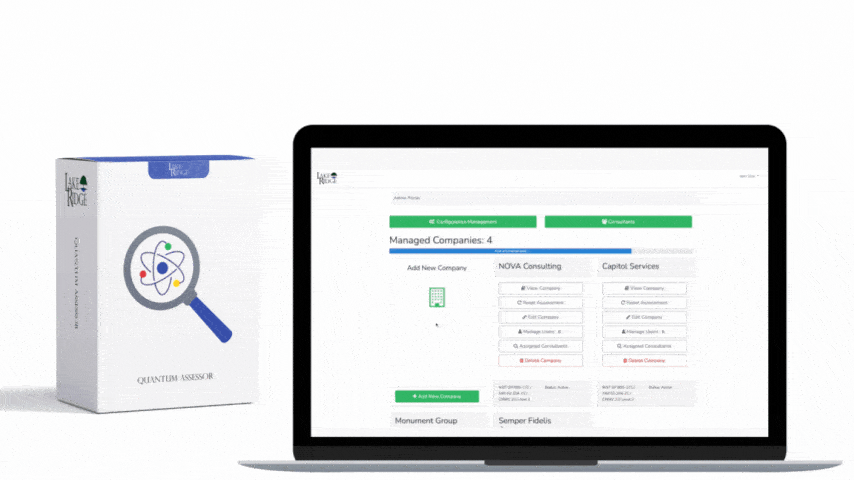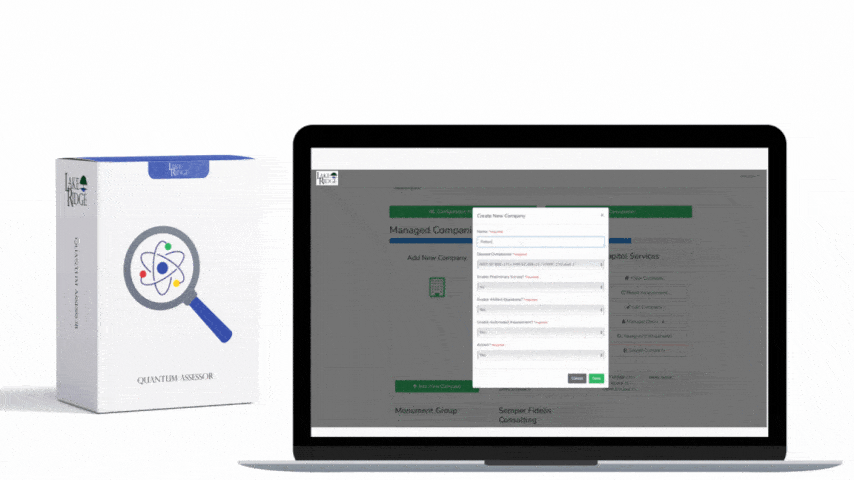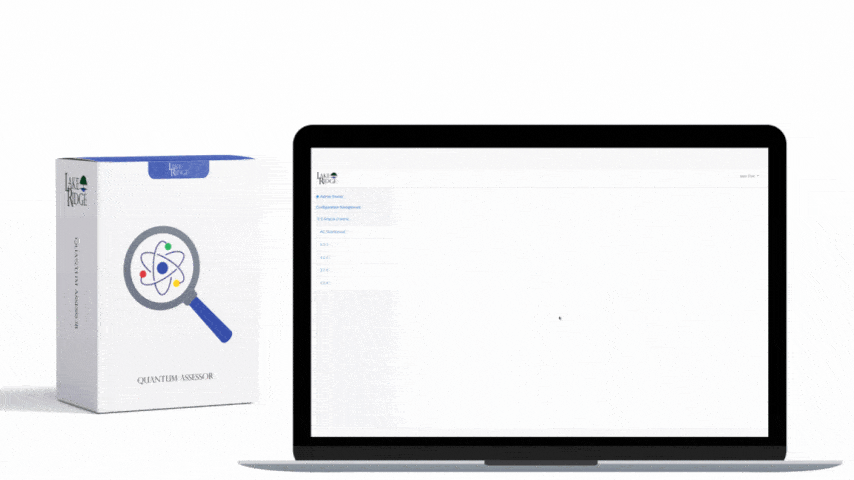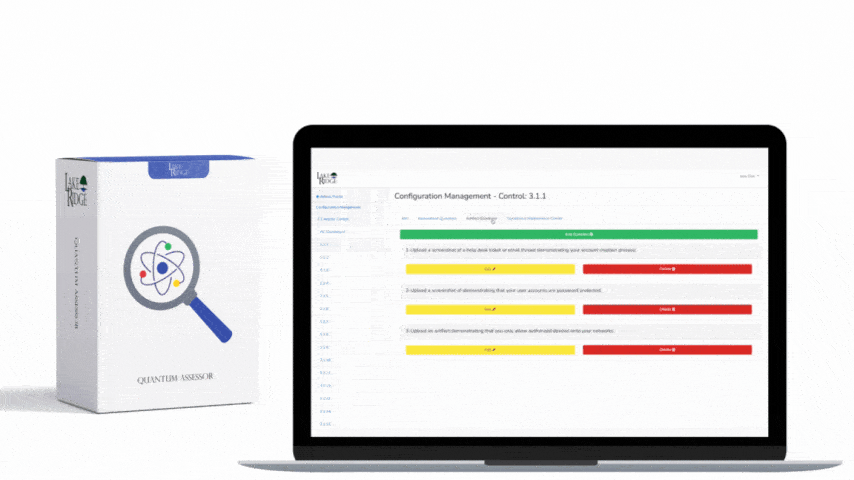
CMMC 1.0 Practice CM.3.068 Requirement:
Restrict, disable, or prevent the use of nonessential programs, functions, ports, protocols, and services.
CMMC 1.0 CM.3.068 Requirement Explanation:
By uninstalling nonessential programs and disabling unused ports, protocols, and services you are reducing the attack surface your systems.
Example CMMC 1.0 CM.3.068 Implementation:
Using your software whitelist (addressed in CM.3.69) as a reference uninstall all non-essential programs from your systems. If it doesn't have an approved business need and isn't on your whitelist, uninstall it. Review your workstations, servers, network devices, and printers to determine which ports and services you can disable. Only leave essential ports open.
CMMC 1.0 CM.3.068 Scenario(s):
- Scenario 1:
You discover that many employees in your organization have iTunes installed on their Windows workstations. Because this is a nonessential program you have it uninstalled from all of your systems.
- Scenario 2:
You have a web server that has several nonessential ports open. You work with your system administrator to only leave the essential ports open.
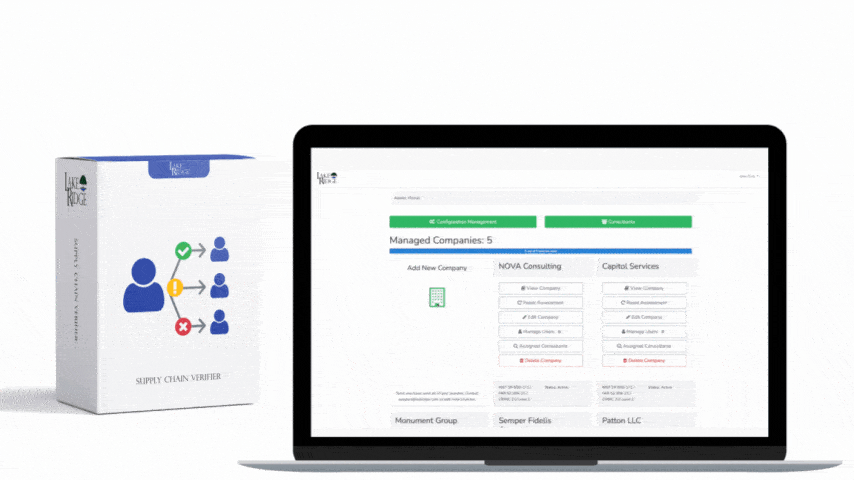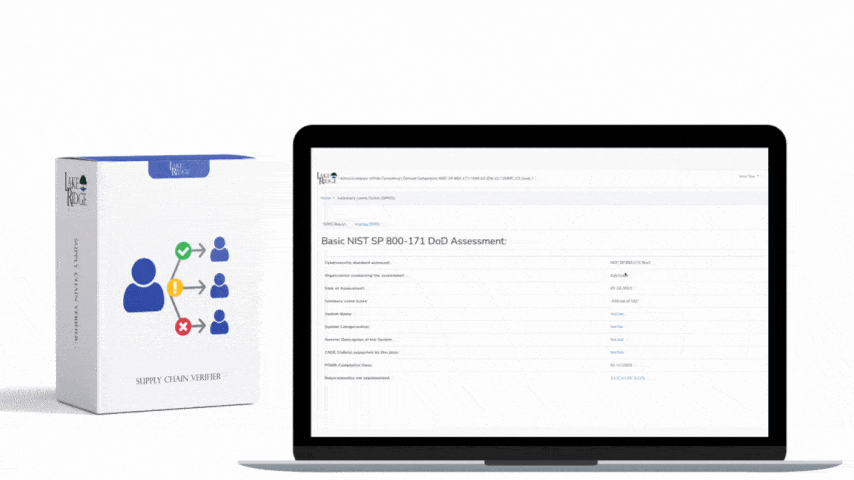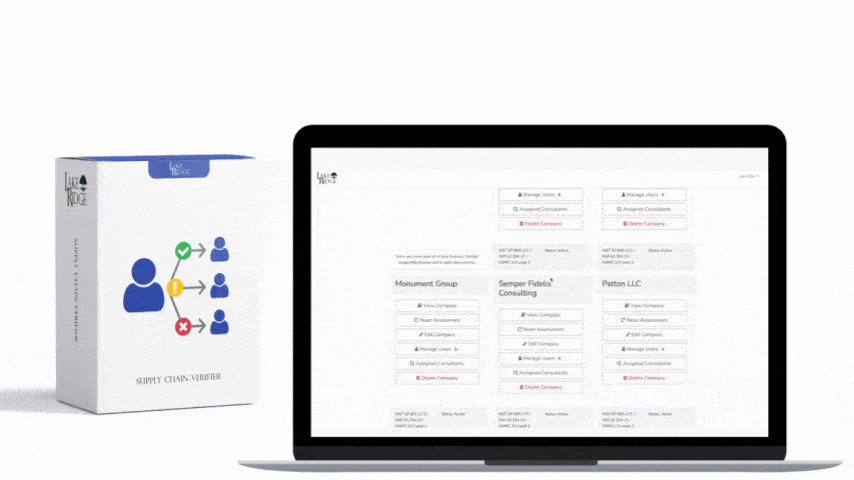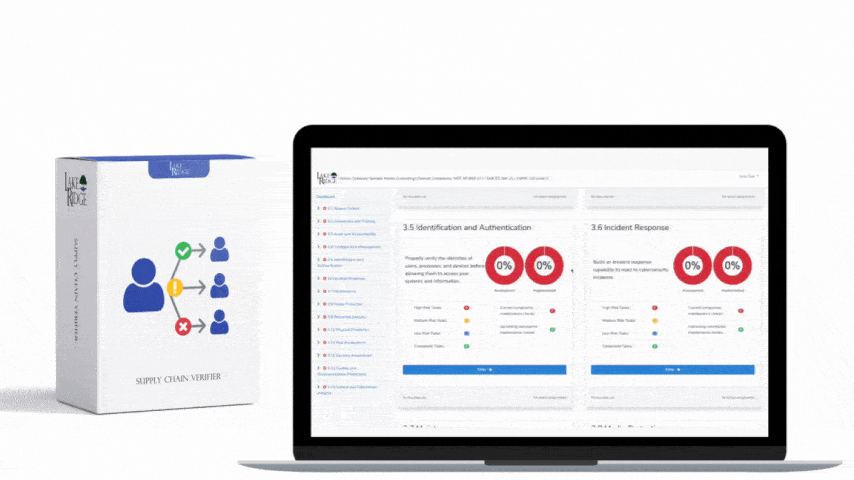
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you