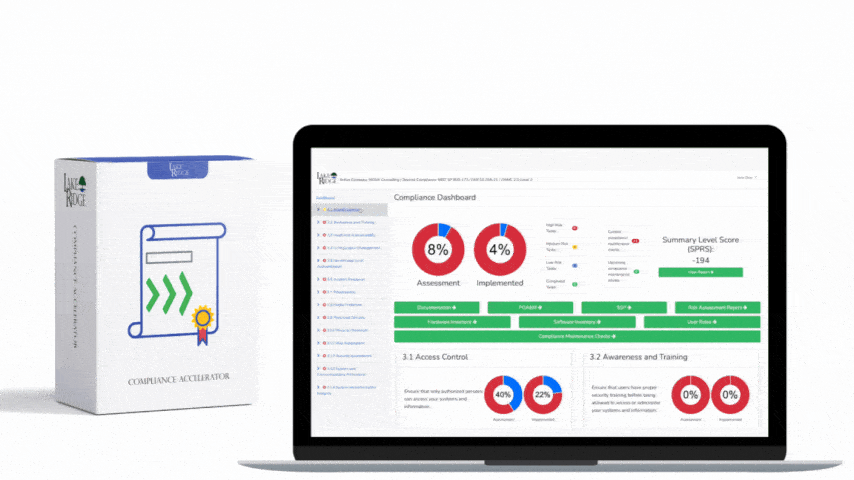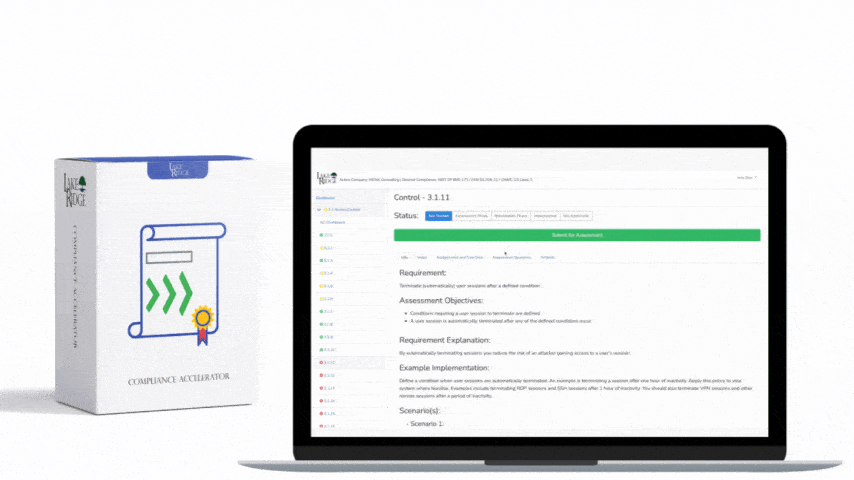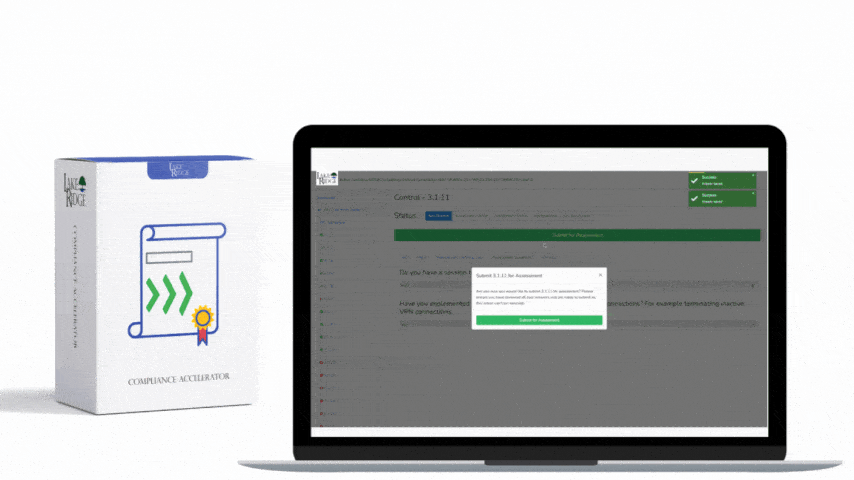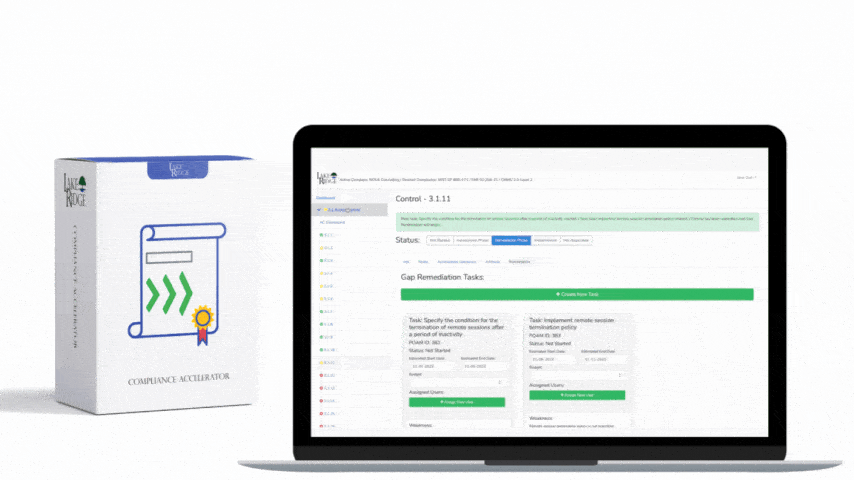
NIST SP 800-171 & CMMC 2.0 3.13.15 Requirement:
Protect the authenticity of communications sessions.
NIST SP 800-171 & CMMC 2.0 3.13.15 Requirement Explanation:
This requirement addresses communications protection at the session level. The requirement intends to protect against man-in-the-middle-attacks.
Example NIST SP 800-171 & CMMC 2.0 3.13.15 Implementation:
Configure TLS on your web servers and VPN connections. Use digital certificates on your web servers and keep the certificates updated. Any web interface you log into should have a green lock in the address bar (TLS with a valid certificate). When users authenticate to a web service or other service over the network they should use two-factor authentication.
NIST SP 800-171 & CMMC 2.0 3.13.15 Scenario(s):
- Scenario 1:
You have a server on your local network that provides timesheet services. When users access the login page they notice the URL of the server includes HTTPS, meaning that it is protected by TLS. It also has a green lock in the URL bar indicating that it has a valid certificate. Both of these security controls protect the authenticity of the user's session to the server. When the user logs into the timesheet they log in using two-factor authentication.
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you