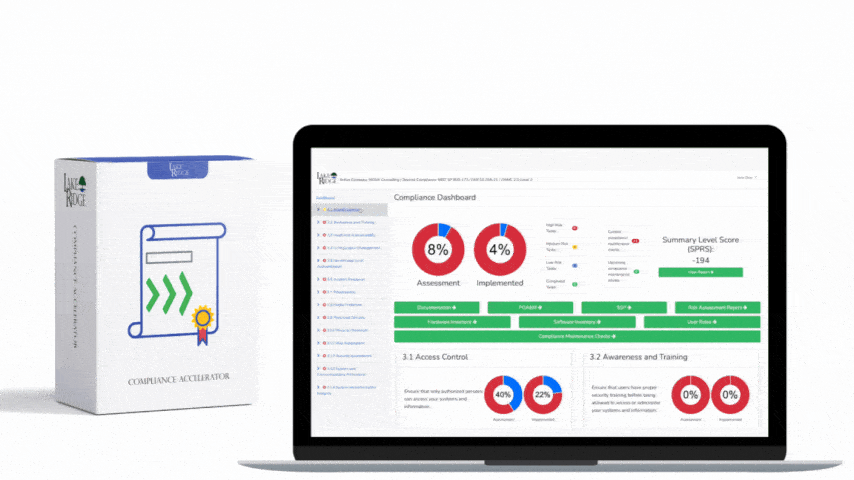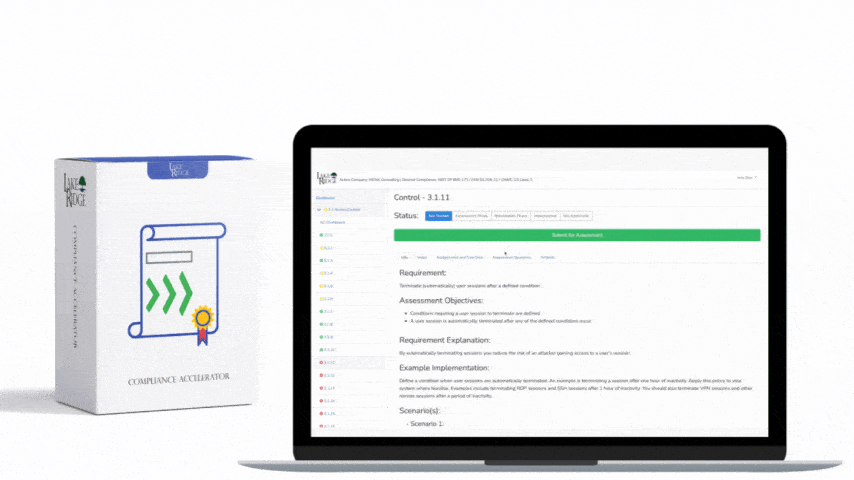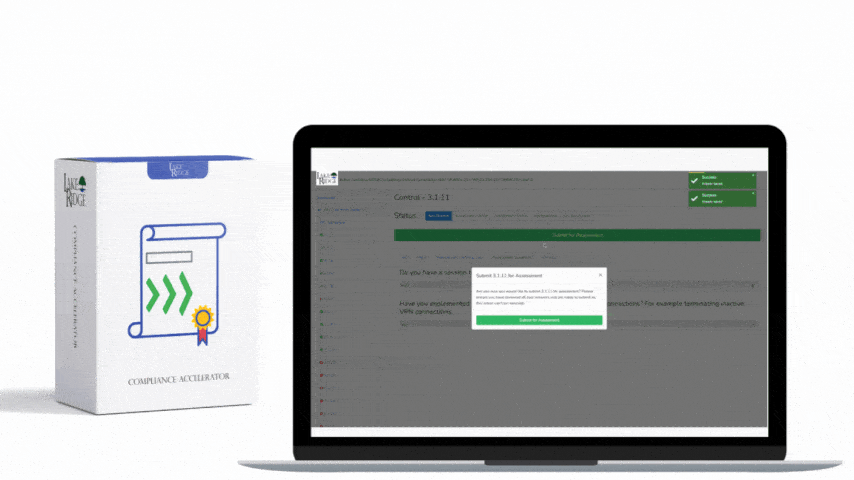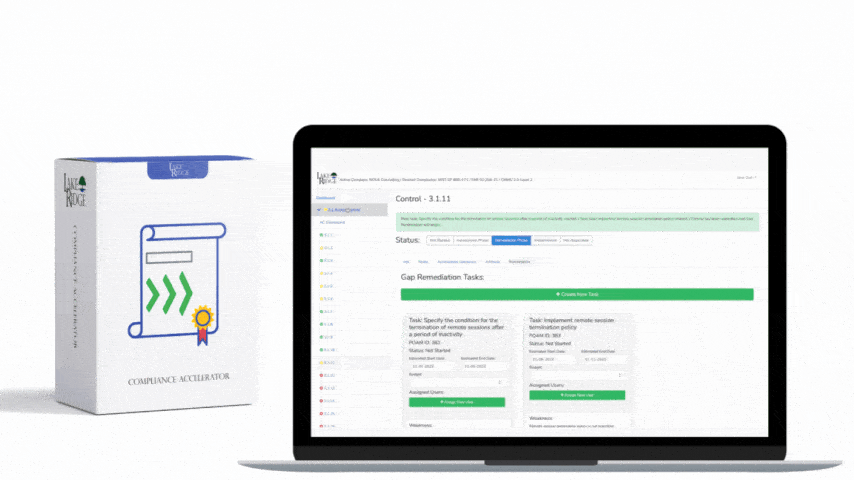
CMMC 1.0 Practice AC.2.007 Requirement:
Employ the principle of least privilege, including for specific security functions and privileged accounts.
CMMC 1.0 AC.2.007 Requirement Explanation:
The principal of least privilege means to restrict user accounts, devices, or services to only the privileges needed to perform their intended function. By limiting the privileges an account has you limit the security risks associated with the account. For example, an unprivileged account can not install software onto a system or modified it's settings as a result it poses less of a risk than a privileged account that can.
Example CMMC 1.0 AC.2.007 Implementation:
Only provide system users the privileges necessary to complete their work. Create user security groups representing the different job roles in your company. Assign the least amount of privileges necessary to the group allowing them to complete their work. Reserve administrative privileges to a limited number of employees. This generally includes IT staff. Revoke administrative rights from as many users as possible. Document any exceptions with a business need.
CMMC 1.0 AC.2.007 Scenario(s):
- Scenario 1:
Alice, a system administrator has decided to revoke local admin rights from the majority of her company's employees. This is because they do not need admin rights to complete their assigned work. Their work generally includes responding to emails and creating word documents. Because admin rights were revoked they can no longer change important settings on their workstations. They can not install software without Alice's permission either.
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you