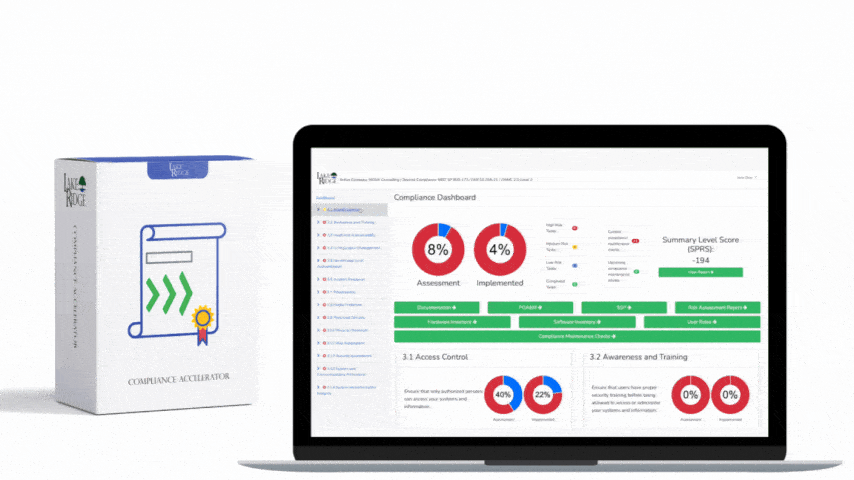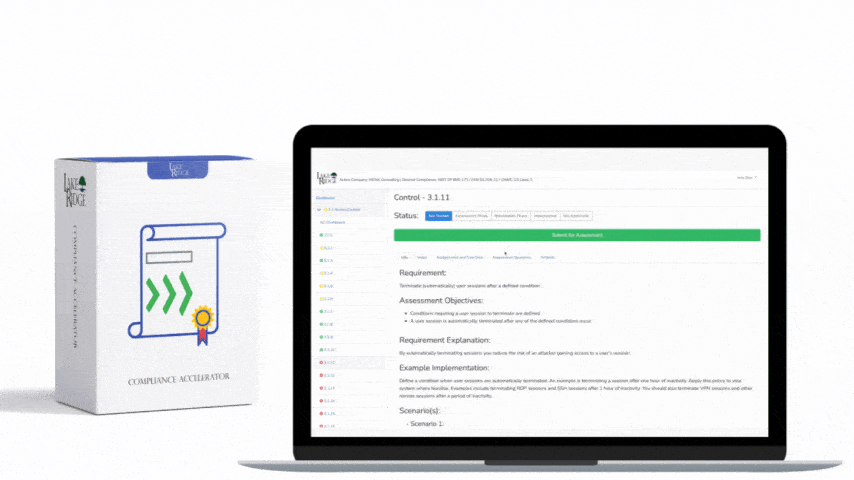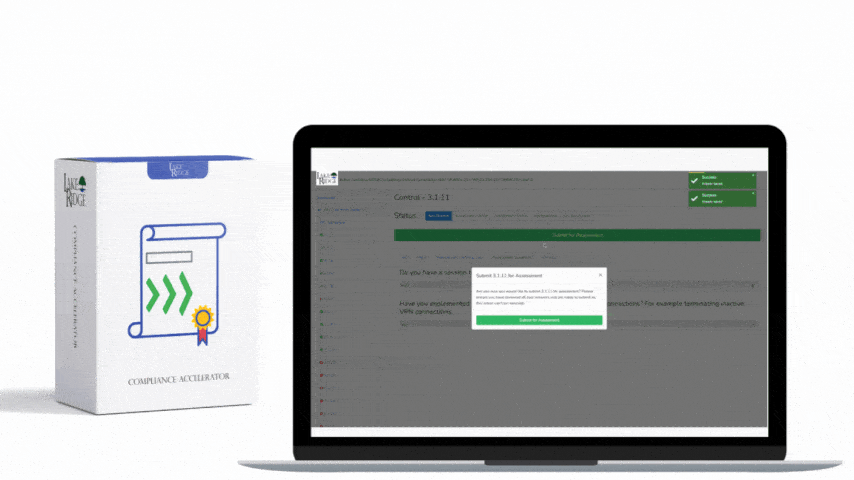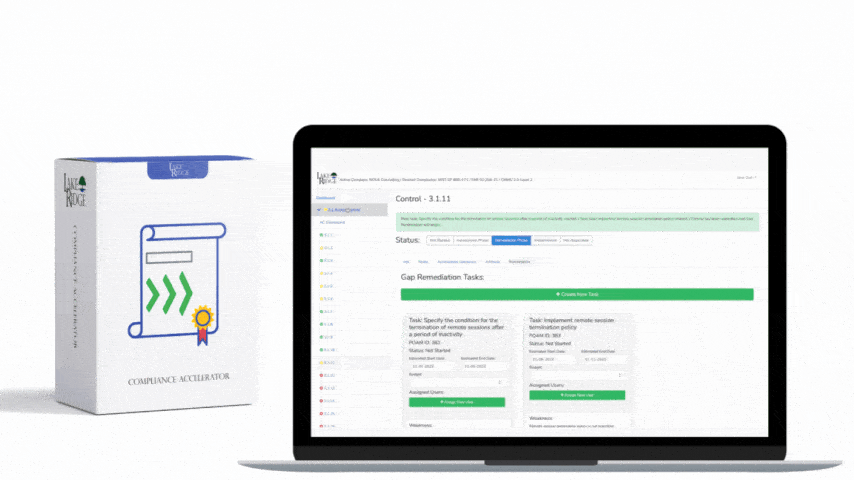
CMMC 1.0 Practice AU.2.042 Requirement:
Create and retain system audit logs and records to the extent needed to enable the monitoring, analysis, investigation, and reporting of unlawful or unauthorized system activity.
CMMC 1.0 AU.2.042 Requirement Explanation:
If a security incident occurs on your systems you will need to investigate it. To effectively investigate you will need to review audit logs. This can only be done if your systems are configured to keep important system and security logs. If you are unsure of what to capture you can use DISA STIGs as guidance.
Example CMMC 1.0 AU.2.042 Implementation:
Configure your systems need to keep audit logs especially security logs. You can use DISA STIGs to help determine which additional events to log. For example, the STIG for Windows 10 lists many audit log settings that you can implement on Windows 10.
CMMC 1.0 AU.2.042 Scenario(s):
- Scenario 1:
Alice, a system administrator wants to capture important logs on her company's Windows 10 workstations. She is doing this so that in the event of a security incident she can conduct an investigation. She decides to implement the audit log settings recommended in DISA's Windows 10 security technical implementation guide (STIG).
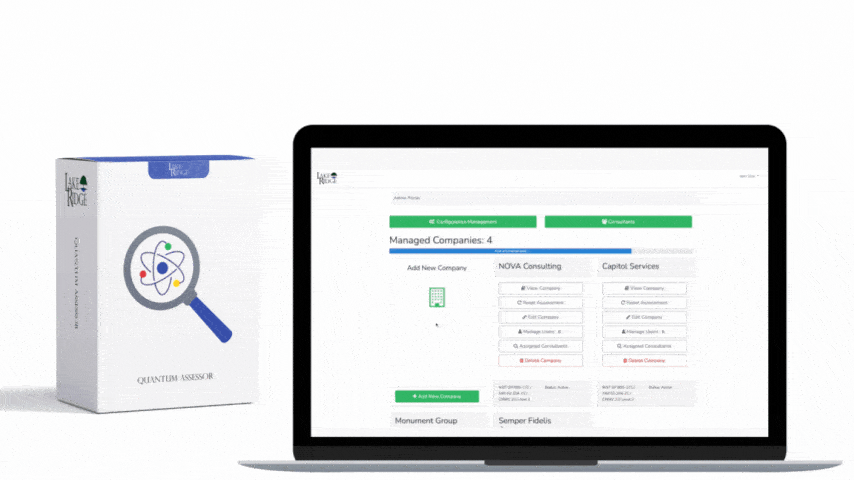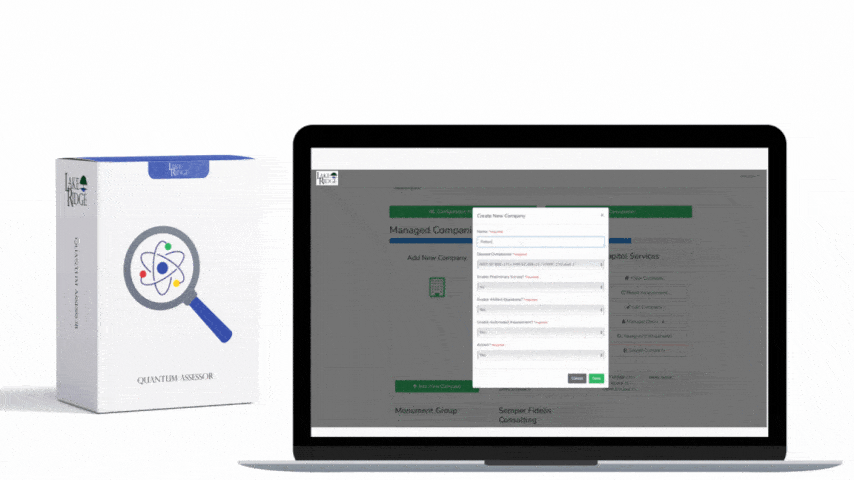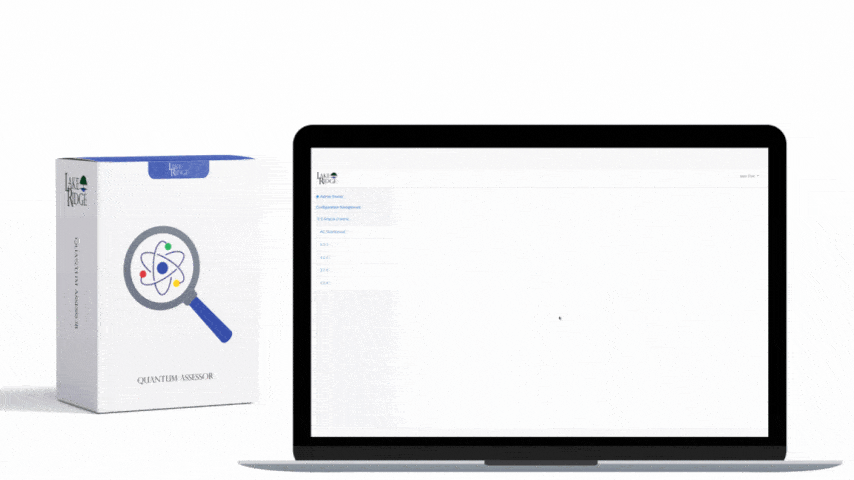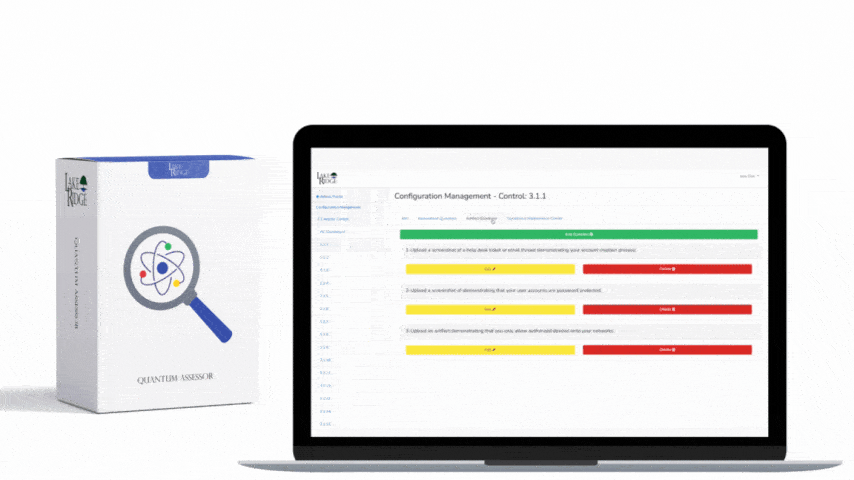
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you