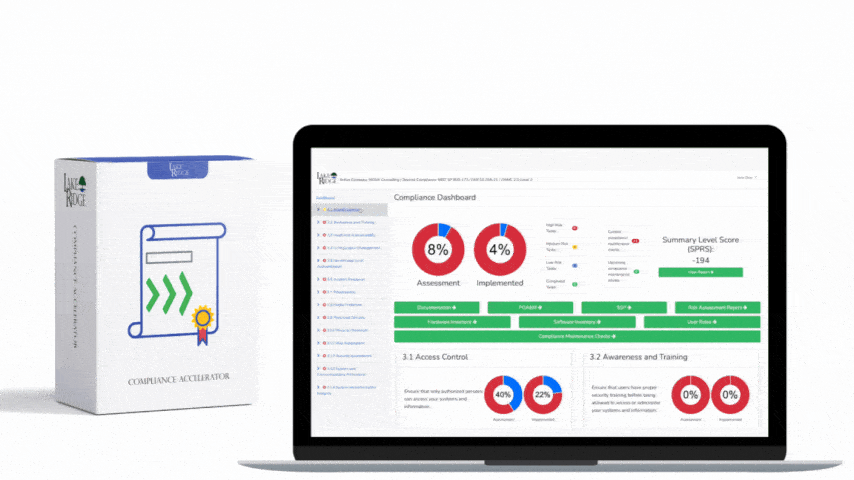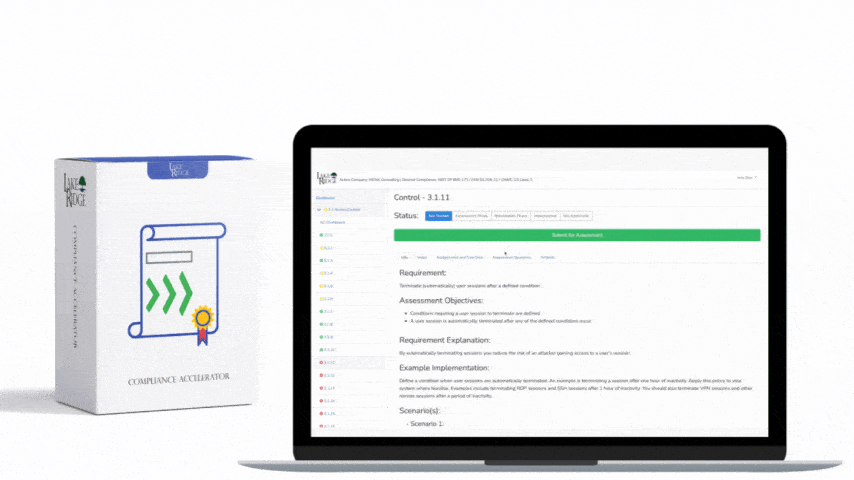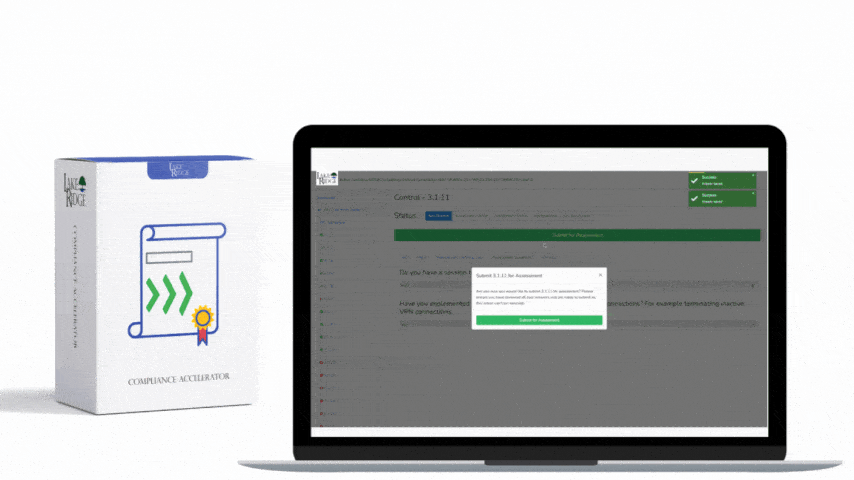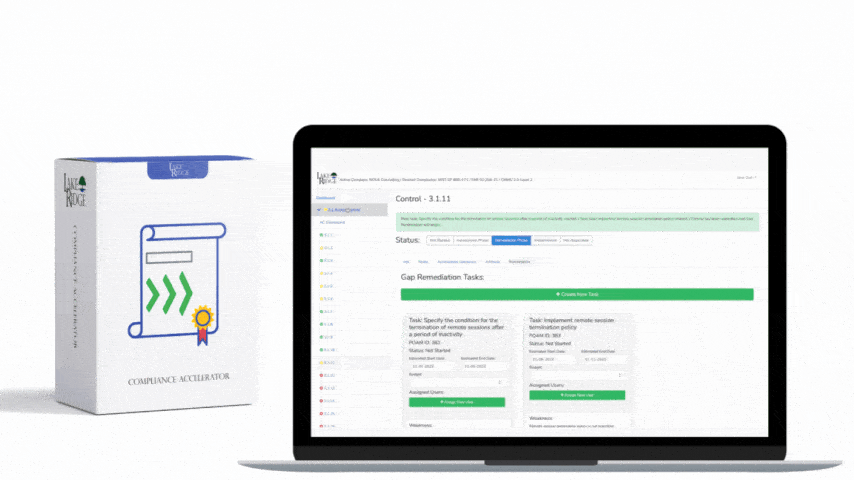
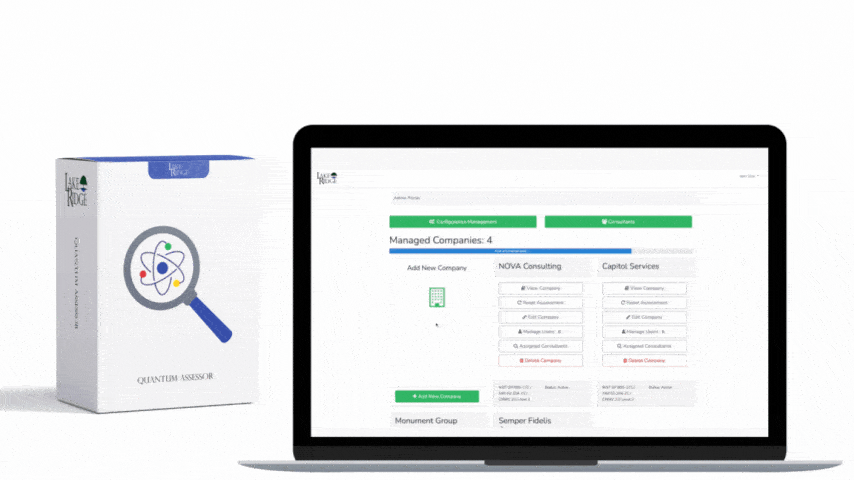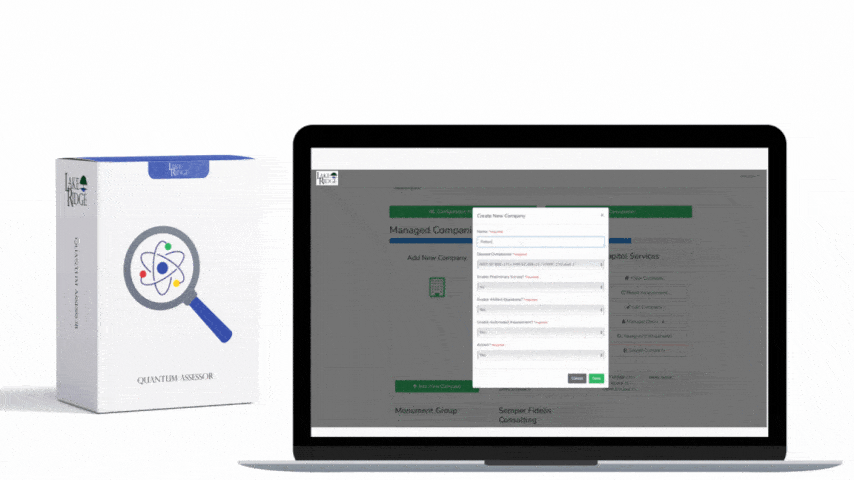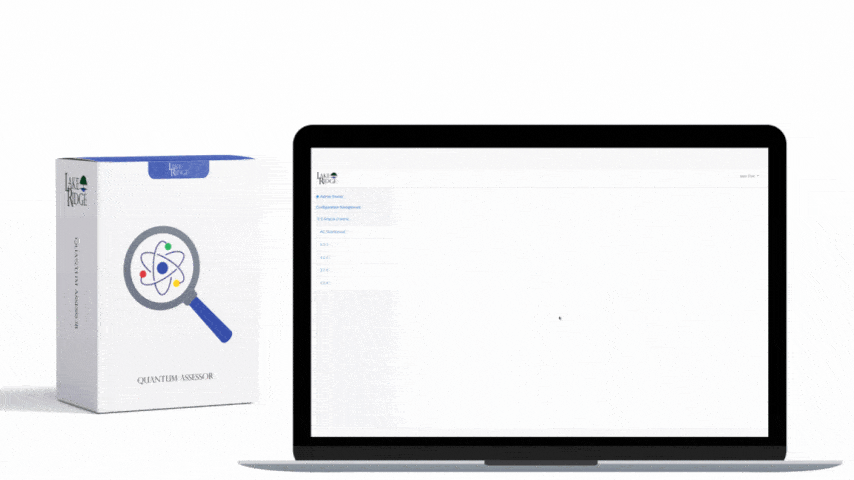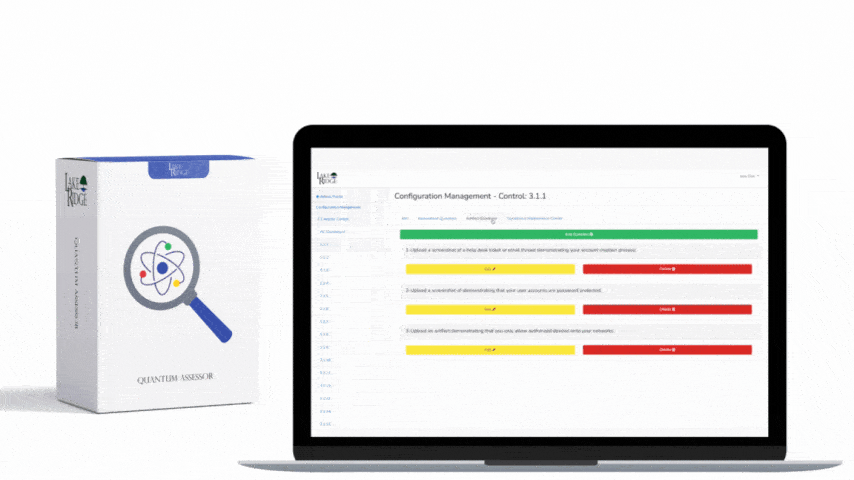
CMMC 1.0 Practice CA.3.161 Requirement:
Monitor security controls on an ongoing basis to ensure the continued effectiveness of the controls.
CMMC 1.0 CA.3.161 Requirement Explanation:
For security controls to remain effective they must be reviewed to determine if they are accomplishing the intended goal. As your systems, businesses process, and people change the effectiveness of your controls may diminish. Ongoing monitoring ensure that issues with your security controls are identified and corrected.
Example CMMC 1.0 CA.3.161 Implementation:
For each of your CMMC practices devise a plan on how to monitor them for their effectiveness. This plan can be in your system security plan. Determine the persons and methods you will use to monitor the controls. Because each CMMC practice is different each may require a different strategy. Establish a policy requiring the monitoring of security controls.
CMMC 1.0 CA.3.161 Scenario(s):
- Scenario 1:
One of your security controls you want to review to ensure its effectiveness is CMMC practice AC.1.002. The practice reads "Limit information system access to the types of transactions and functions that authorized users are permitted to execute.". To monitor the effectiveness of this control you review security group memberships to verify that the accounts in the groups align with their assigned duties.
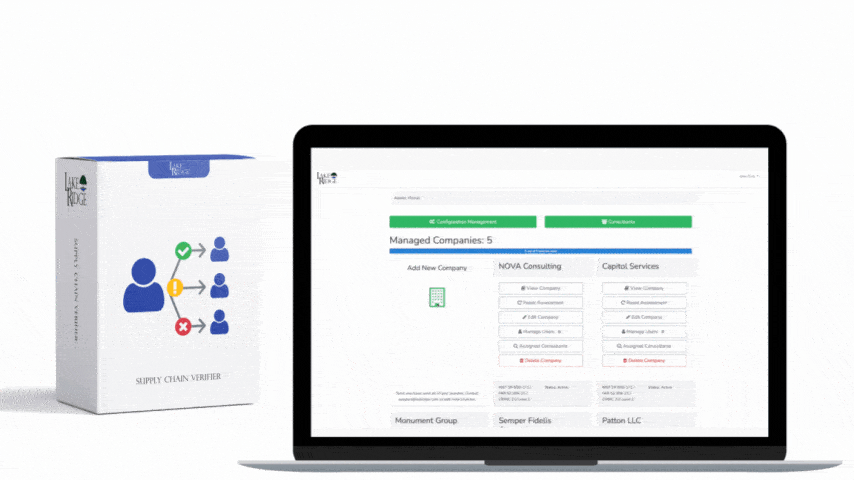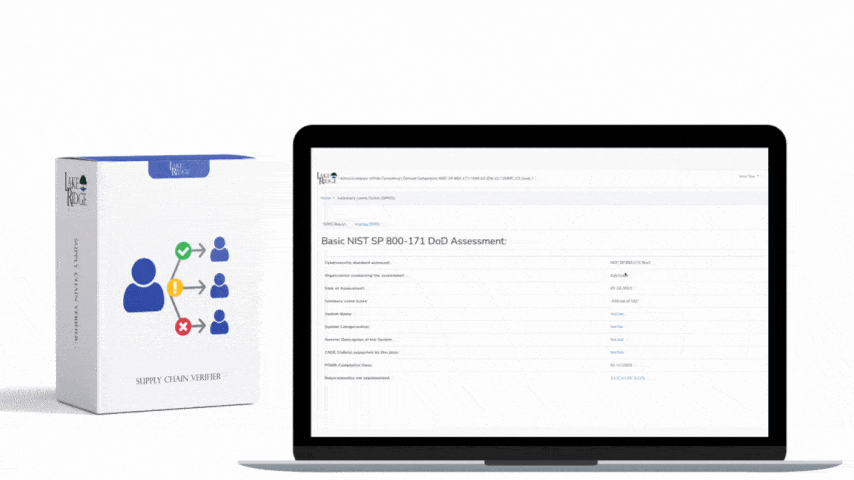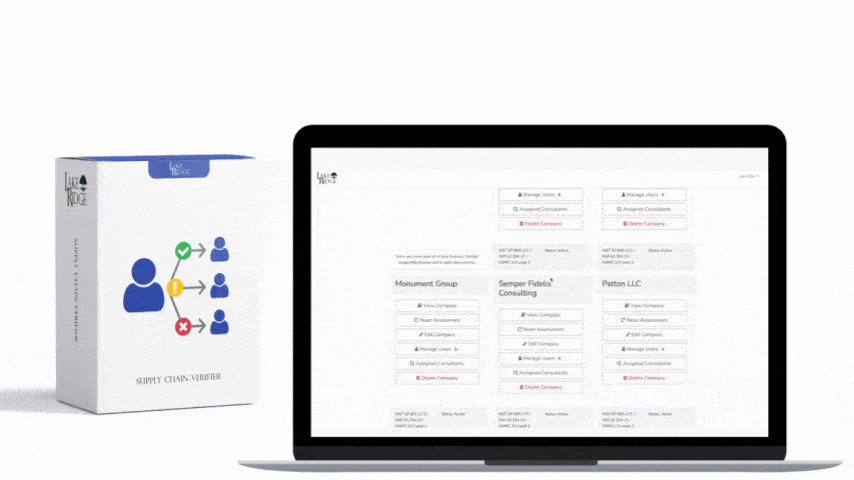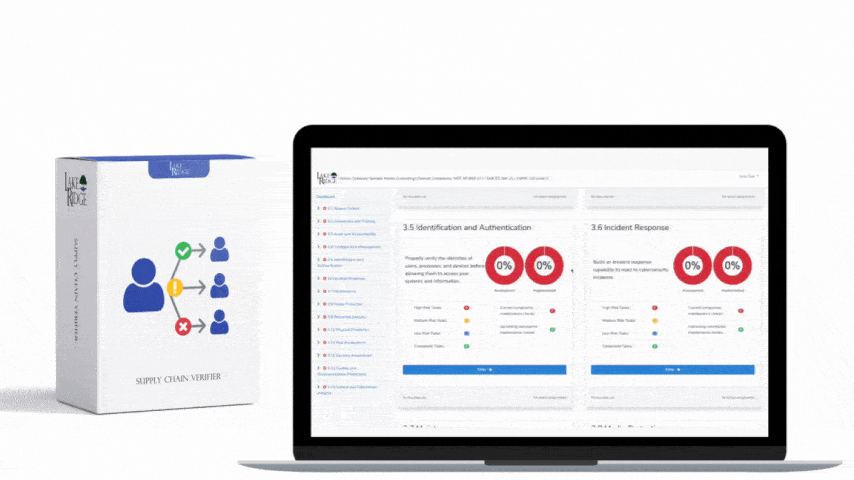
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you