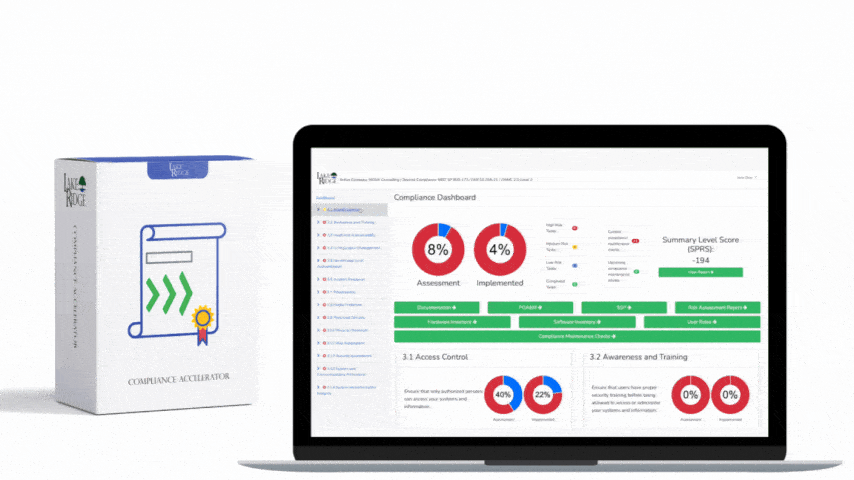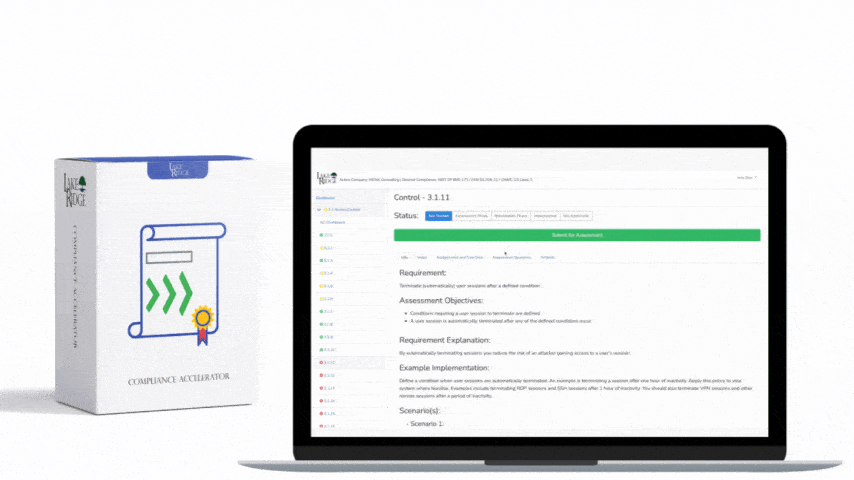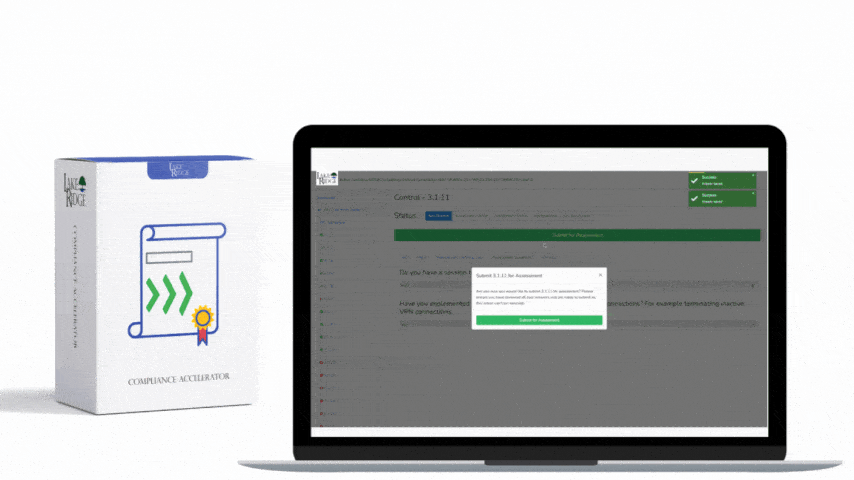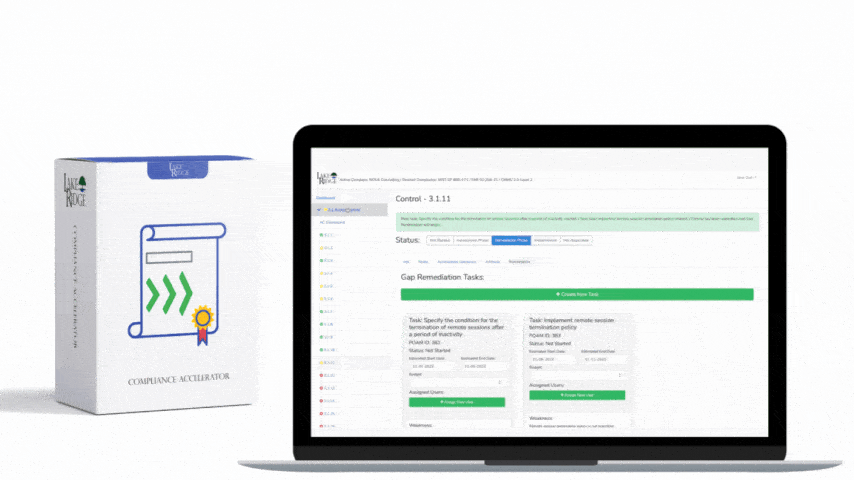
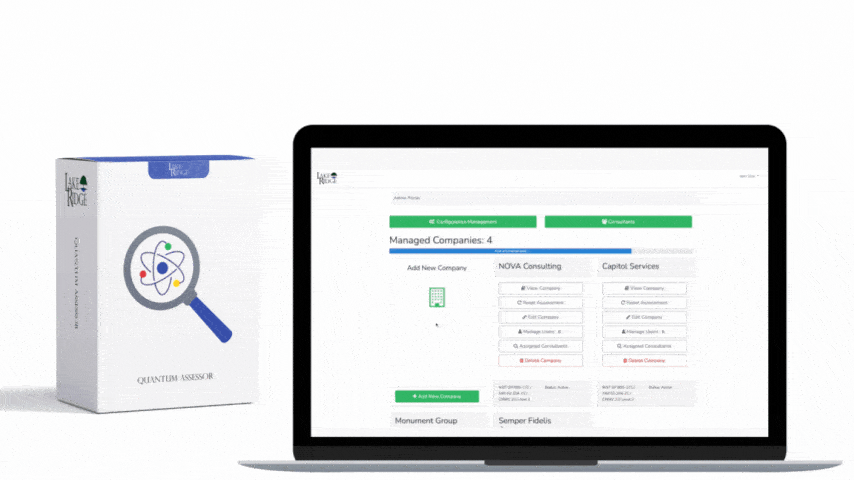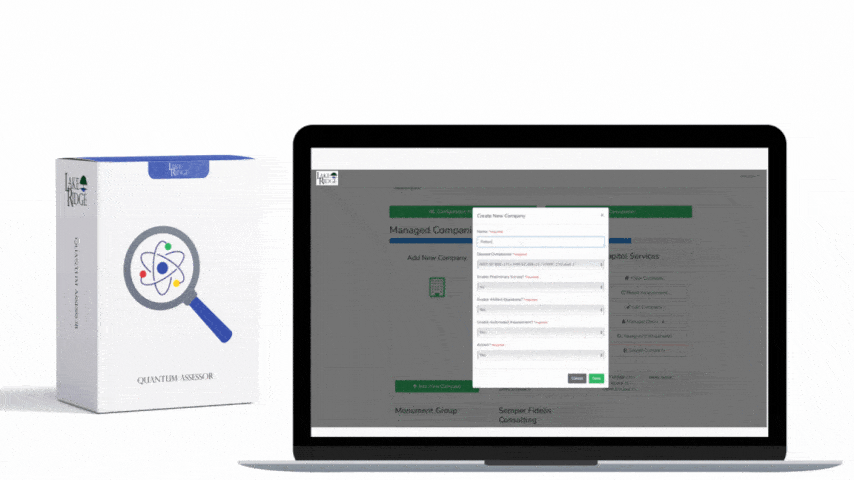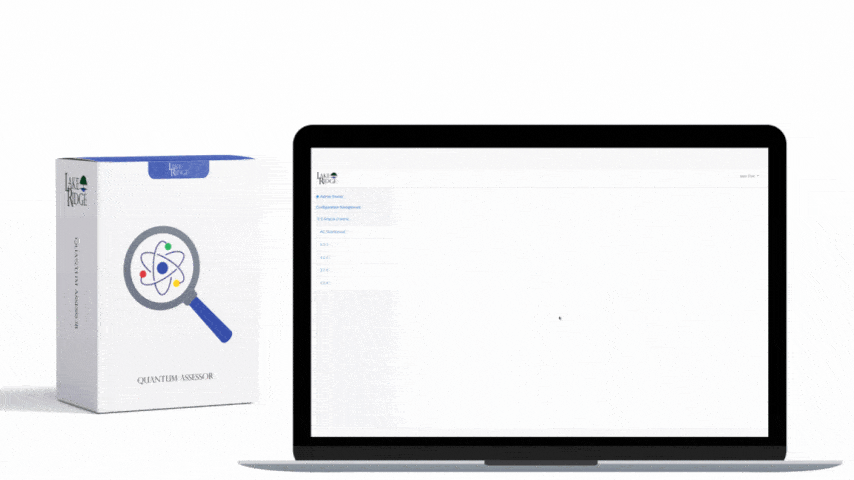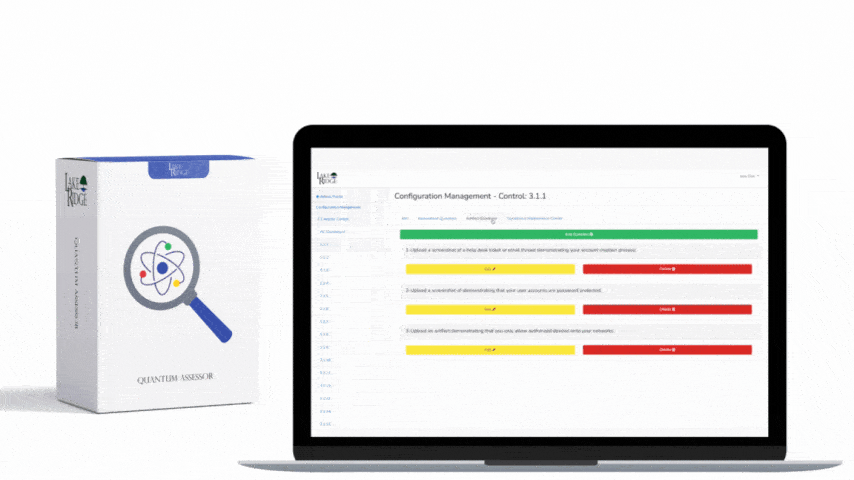
CMMC 1.0 Practice SI.3.220 Requirement:
Utilize email sandboxing to detect or block potentially malicious email attachments.
CMMC 1.0 SI.3.220 Requirement Explanation:
Sandboxing separates emails from your system while they are scanned for malicious links and attachments. If the email is deemed to be malicious it will be blocked. This prevents users from falling prey to phishing attacks.
Example CMMC 1.0 SI.3.220 Implementation:
Make sure the email service you use, scans emails for malicious attachments. Services like G-Suite and Office 365 do this automatically for their email services. For Office 365 you can purchase advanced threat protection, providing you with more capability. If your email service does not scan files for malicious attachments, then you will need to purchase a tool that does.
CMMC 1.0 SI.3.220 Scenario(s):
- Scenario 1:
Your employee received an email with an attachment. Because the attachment was malicious he received a notification that the attachment has been blocked.
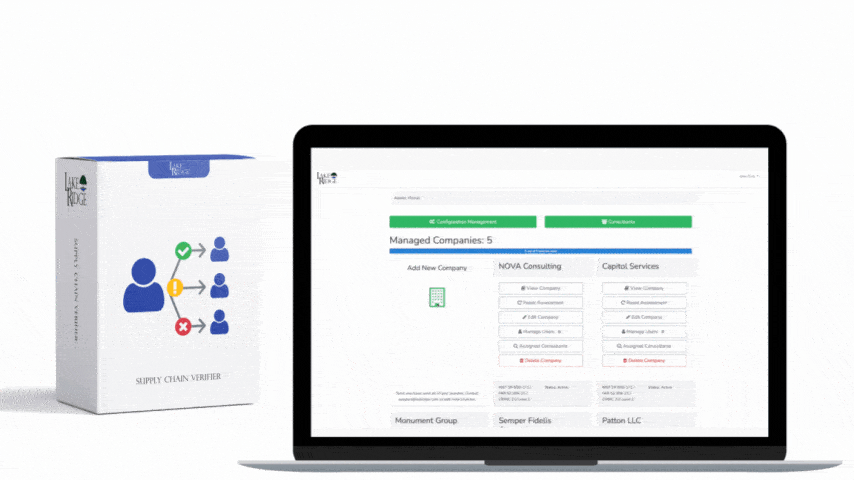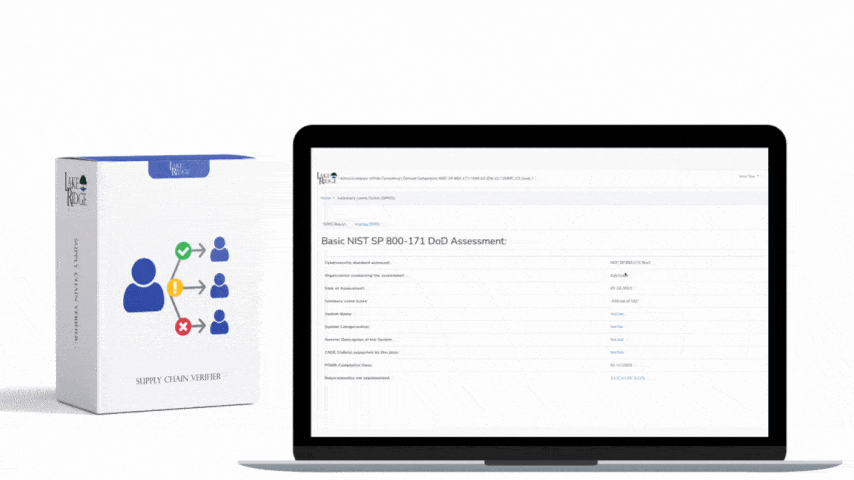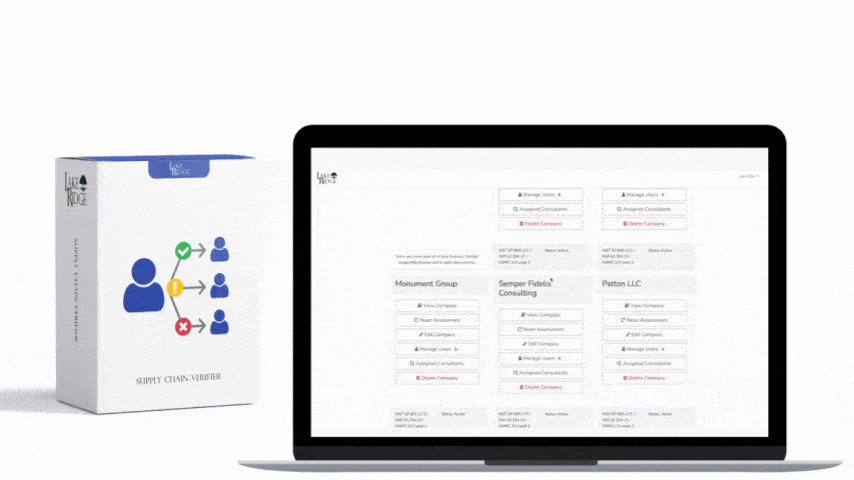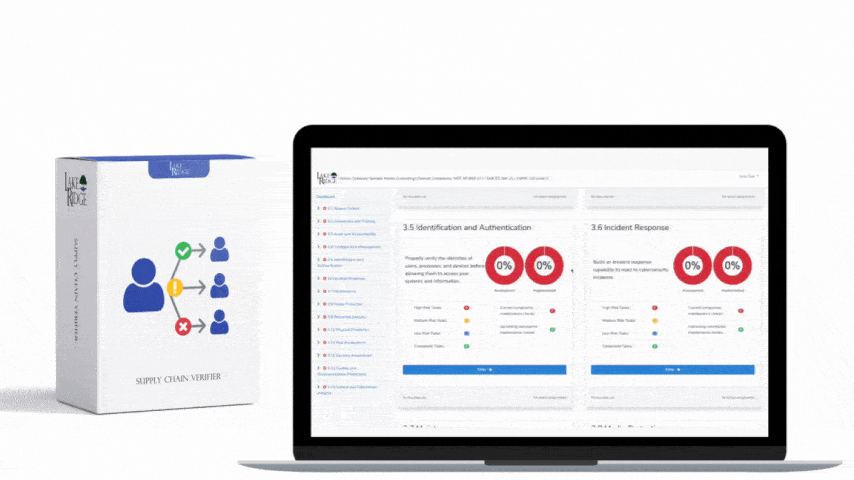
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you