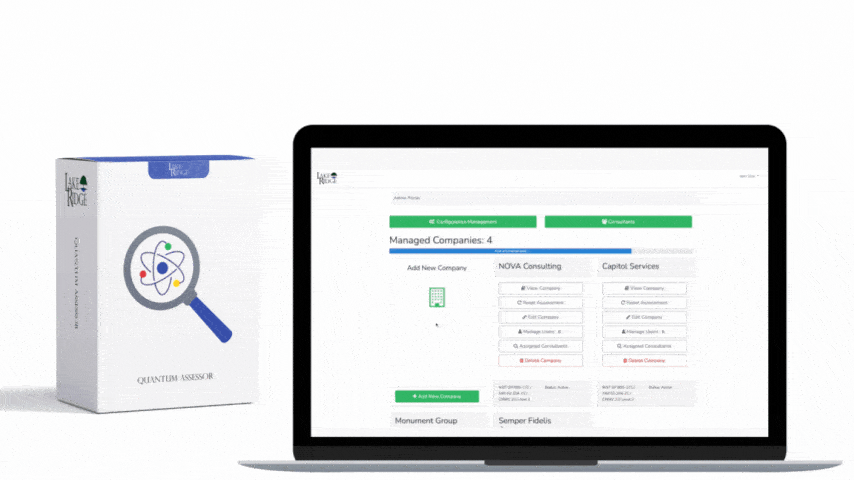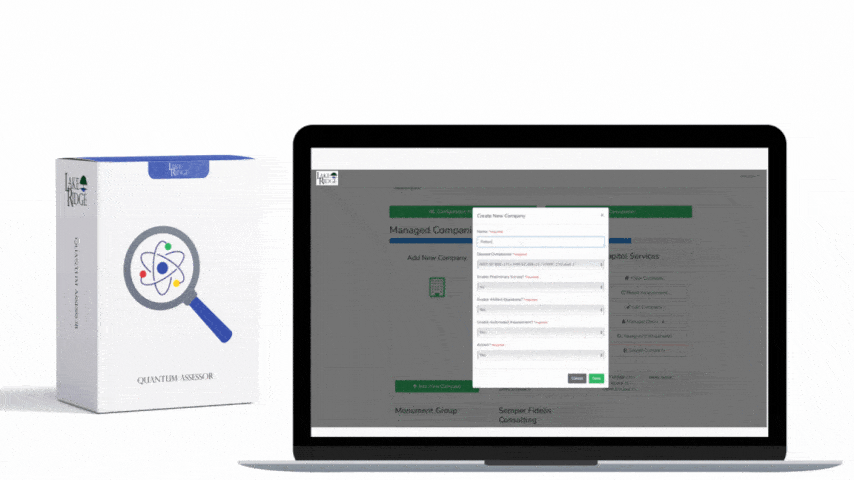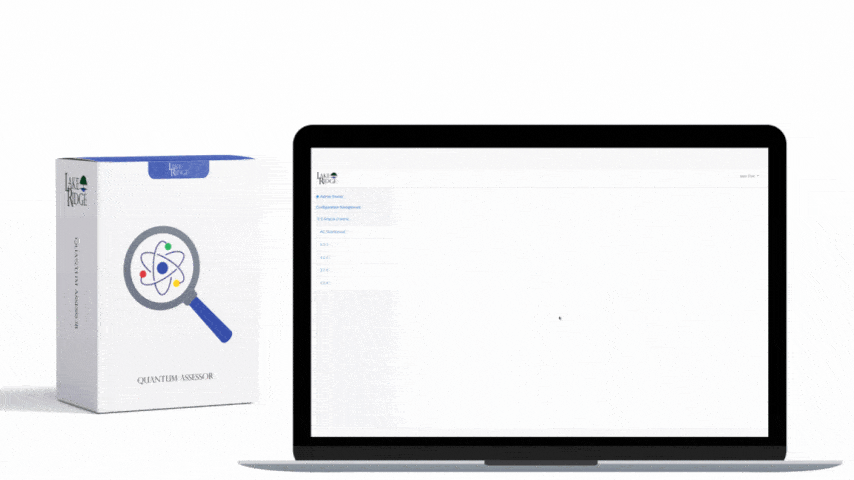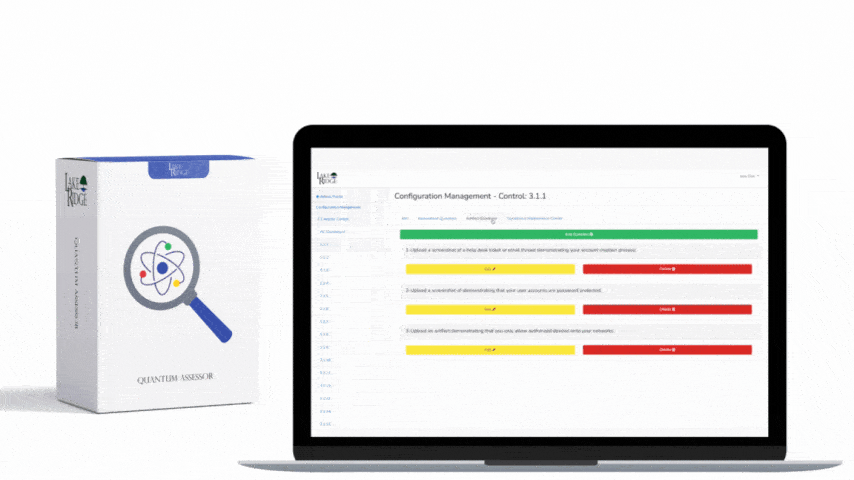
NIST SP 800-171 & CMMC 2.0 3.1.1 Requirement:
Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
NIST SP 800-171 & CMMC 2.0 3.1.1 Requirement Explanation:
You need to identify users, processes, and devices that are allowed to use company systems. Only authorized users, processes, and devices should be allowed to access your information system. Users include employees and contractors. Processes include automated scripts such as scripts that run updates or other tasks. Devices include computers, printers, servers, and network devices.
Example NIST SP 800-171 & CMMC 2.0 3.1.1 Implementation:
Maintain a list of persons who are authorized to access your system. You can use our System Access Authorizations documentation template to do this. You need to review all your system accounts and delete/disable any accounts that should not have access to your system. You need to develop an account creation process to ensure that going forward, only authorized persons are provided with accounts to log onto your system. You need to remove unauthorized devices from your network.
NIST SP 800-171 & CMMC 2.0 3.1.1 Scenario(s):
- Scenario 1:
Alice is responsible for creating user accounts. She follows her IT team's account creation process. The process only allows authorized persons to be given a user account. Every account Alice creates is password protected so that only the intended person can use it.
- Scenario 2:
Alice is a system administrator. She receives word from human resources (HR) that an employee will be terminated today at 3:00 PM. At 3:00 PM Alice disables his user account. The former employee no longer has access to company systems.
- Scenario 3:
Bob decides to bring his personal laptop to work and connect it to the corporate network. Alice, a system administrator, notices that an unauthorized device has connected to the network. She blocks the MAC address on her DHCP server to prevent it from connecting to the network. Bob submits a help desk ticket stating that he can't access the network. Alice responds to the ticket and discovers that she has blocked Bob's personal device. Alice tells Bob to use his work computer as personal devices are not allowed on the corporate network.
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you